So here we have another phishing setup we discovered as part of the "Fried Phish" project, this time targeting customers of Cox Communications, an ISP and TV provider in the United States. This phishing setup was designed to capture login credentials and billing information of Cox customers, presumably for the purpose of credit card fraud and identity theft.
Again, this phishing page was delivered by spam emails. Unfortunately, I don't have a copy of the original phishing email, but that doesn't matter much. The general gist of it was that your Cox account had been suspended or deactivated and that you had to log back in and update your billing details. This is actually a surprisingly effective lure for people.
So when you click on the link you are sent, you end up landing on the following login page, which purports to be the login page for your Cox account.
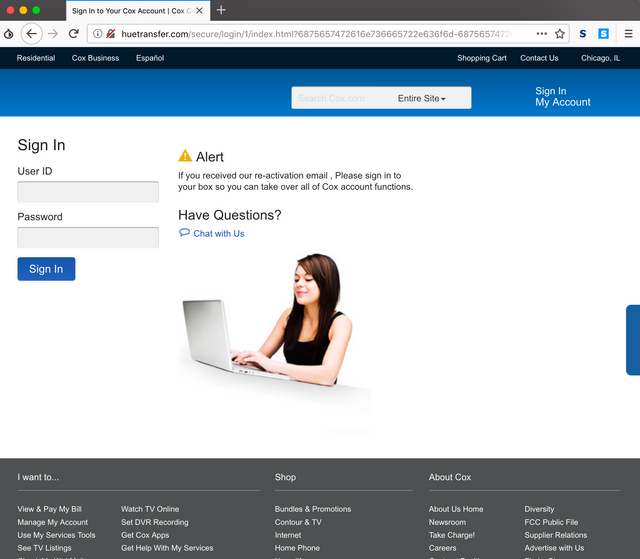
Once you log in (we just entered some bullshit here), you will get redirected to another page, which asks you to update your payment information - i.e. your credit card and some other information. They also request your mothers maiden name and social security number, which are incredibly useful for committing further fraud.
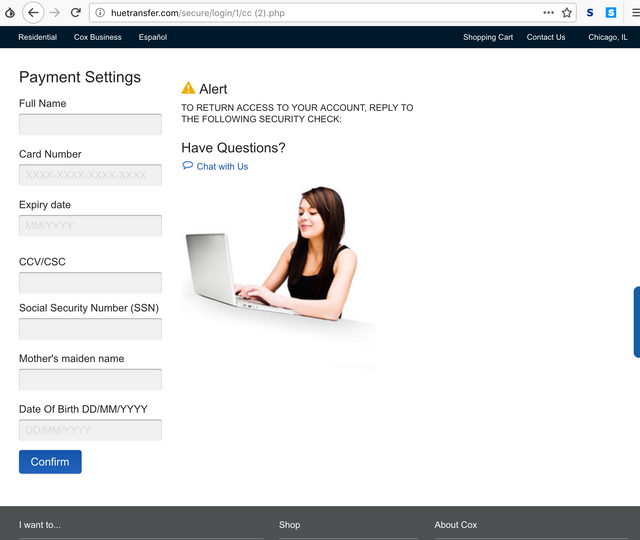
Once we filled in some BS card details and the likes, we got bounced along to another page, which asked us for our address, driver licence number, and some other stuff. All very, very useful to an identity thief.
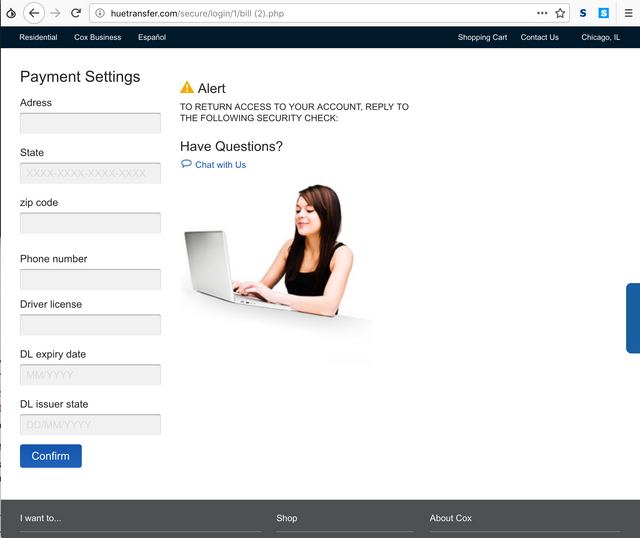
Once you finish filling in that form, it simply redirects you along to the legitimate Cox website to prevent you from getting suspicious.
So we decided to see if we could obtain a copy of the phishing panels source code, and began traversing directories in the hopes of finding a copy of it. Unfortunately, this time we did not get a copy of the panels source, however we did find something else interesting in a directory with indexing enabled.
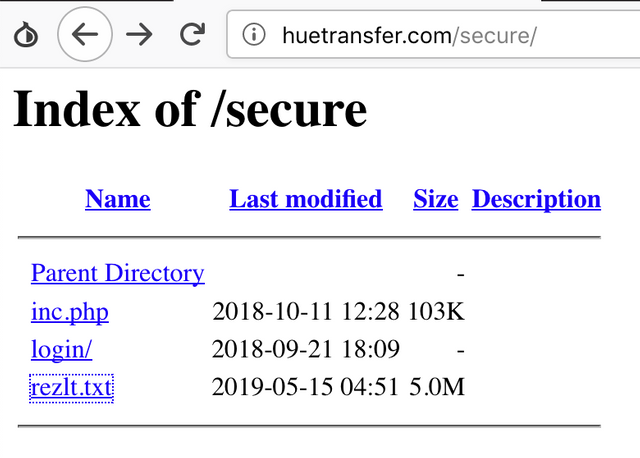
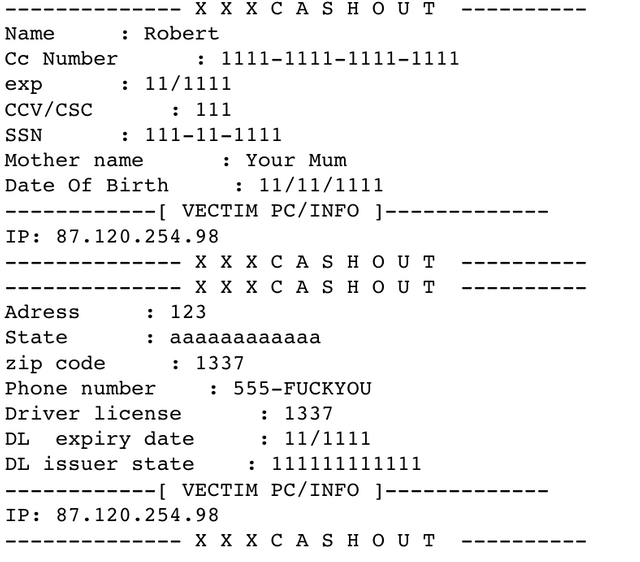
We wondered what could possibly be in the file "rezlt.txt", so we decided to view it. Inside, we found a tonne of actual Cox login credentials and some credit card details, along with some garbage, and the fake information we entered. So instead of emailing the credentials to the attacker like in the Maersk kit, this one just logs them to a file. The screenshot below shows the fake login credentials and personal information we entered.
We also wanted to find out what is the "inc.php" script in the directory, so we decided to have a look at it. Turns out, its a bulk mailing script that uses the webserver to send spam emails, named "PHP MAILER 2015".
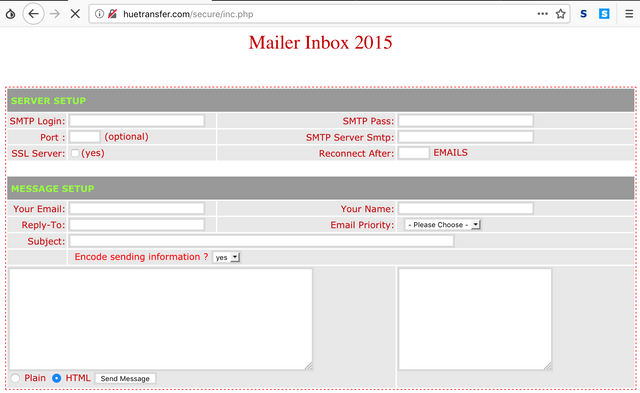
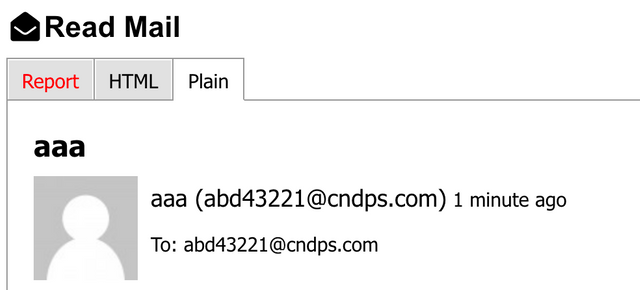
We quickly set up a 10minutemail address, and decided to test the mailers functionality. As you can see, it did actually send an email.
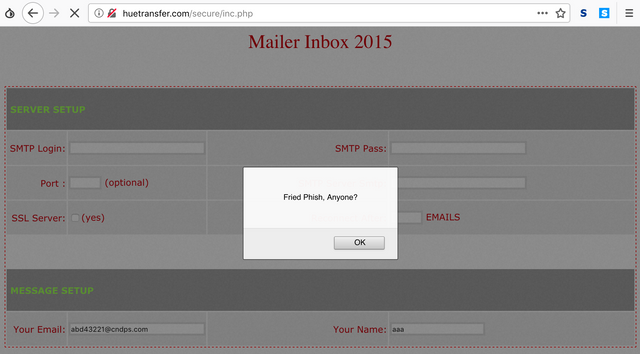
While playing with the mailer script, we couldn't help but notice it was vulnerable to cross-site scripting (XSS) attacks, indicating that whoever programmed the panel did not do so with security in mind.
So that is all for now, showing you the behind the scenes of how another rather crude phishing campaign operates. I'll hopefully soon have more examples to share with you all, along with some contact details for reporting phishing campaigns you come across to us so we can investigate and expose their inner workings. We are especially keen to find some good examples of scammers targeting the cryptocurrency community!
If you would like to see more content like this, let us know in the comments section below!
Congratulations @balor! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit