It seems that the NotPetya ransomware that yesterday hit European companies, including a large majority of Ukrainian infrastructure, has been more or less mastered. But if you fear that this malware will come back again - which is not to be excluded given the multiplicity of methods to spread it - there are some measures to stop future attacks.
One way to prevent a PC infection is to "trick" the malware, making it believe that it is already present on the computer. A realizable operation by going to C: Windows and creating a file named "perfc" (which will eventually look like% WINDIR% perfc) and then put it into "read-only". According to Hacker House CEO Matthew Hickey, this will be enough to protect your PC. Indeed, in the process of malware operation, it first searches for the name of this file. If he finds it, he will "commit suicide," said Cybereason, one of the two cyber security companies (with Positive Technologies) responsible for finding a "vaccine."
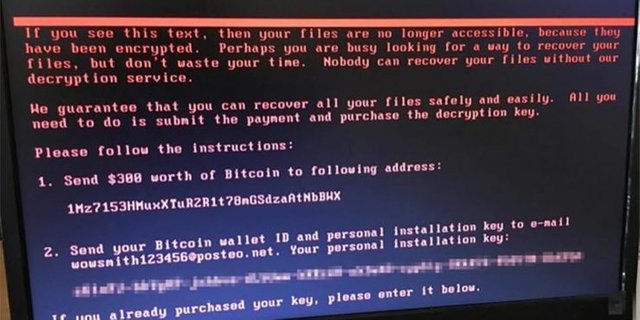
Matthew Hickey also recommends that users check if their computer is already infected, and if so, if the ransomware is not already running. To do this, locate two files that are running in Windows Task Manager, named "rundll32.exe". If they are present, turn off your PC and do not turn it on again under any circumstances. If you turn it back on, the ransomware will run, encrypt your files and ask you for $ 300 in Bitcoin to unlock them (do not pay: the email account of hackers used to manage payments and provide encryption keys has been closed) .
Reinstall Windows will then remove NotPetya from your device. With luck, you have backups to recover files from your PC, whether on a device or on the cloud. If not, there is a way to recover unencrypted data, via free Kali Linux distribution. Launch it to access your computer's hard drive before reinstalling Windows, says Matthew Hickey.
Last but not least, you have to maintain an irreproachable level of digital hygiene. In particular, make sure you are up-to-date on the version of Windows you are using, the latest updates fixing the flaws that ransomwares like NotPetya and WannaCry exploit (vulnerabilities revealed by Shadow Brokers, who claimed that these bugs Were originally operated by the NSA). Verify that the Windows Firewall is enabled, that your anti-virus is up to date, and that all your third-party software is also up-to-date.
For businesses, you can disable two tools used during these attacks - Windows Management Instrumentation and SMBv1. "The attacks used a software update to spread. Thus, even when you follow all these precautions, there is a risk of infection. So make sure that the update programs do not contain suspicious files, "adds Hickey.
64 countries affected by NotPetya
Although Ukraine was the main target of NotPetya, with at least 12,500 infected PCs, Microsoft said 64 countries were also affected, including Belgium, Brazil, Germany, Russia and the United States, United.
Microsoft also pointed out that MeDoc, a Ukrainian accounting software supplier was the primary source of the attack. Costin Raiu, from the Ukrainian news site Kasperky Lab (for the local newspaper Evening Bakhmut), said that they had been victims of the hack, and probably used to spread it.
Although they have been considerably reduced, the chances of infection remain. Among the latest victims were very large companies, including the BNP Paribas bank and Auchan supermarkets.

Good to know
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit