Blockchain in simple words is a distributed #ledger #technology. A ledger in accounting terms is a document that records the financial transactions. The #blockchain can essentially record the financial transactions or any other information. Hence now many have started referring blockchain as distributed database. The beauty of blockchain is that by using the basic cryptographic principles the records can be made temper proof, and hence can be stored over network across millions of computers, that provides resiliency (no single point of failure) and de-centralization, and the entire network provides the transparency and trustworthiness via consensus mechanism (covered below).
Why it is called so:
Blockchain is so called because it stores the data in blocks. A block can contain many records/transactions. The blocks are associated with each other in chain like structure (you can visualize it like a linked-list). The blockchain can be represented something like below :
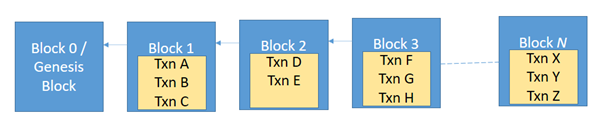
Please note: the Block 0 or the “Genesis Block” is the starting block of the chain, and the blocks are linked with the previous blocks and not the next block (ie block 3 will have the id/hash of block 2).
How it Works:
Blockchain itself is of little use, unless coupled with other supplementing technologies /infrastructure (covered in detail below). Two important concepts of computer engineering: peer-2-peer and cryptography play an important role in functioning of block-chain. Since crypto-currencies provide most common use-case for block-chain, lets use one such example:
Person A wants to transfer 100$ to his family member Person B
Step 1: In the blockchain world, since the transaction will have to move through the untrusted set of computers (via peer-2-peer networking), it needs to be protected so that money only reaches Person B. Here cryptography kicks in:
a. The person A needs to generate a public-private key pair (asymmetric cryptography) that is unique to person A.
b. Create a encoded message (Msg) that represents the transfer information something like this:
Msg = Sender : Person A , Receiver : Person B , Amount : 100 , currency : USD
c. Sign this message with his private-key :
Sign = sign (msg, private-key) // A hash value
d. Creates a Transaction (Txn) with Msg+Sign. Also adds a unique transaction-hash that acts as an identifier for the transaction
e. Broadcasts the transaction(Txn) to Peer-2-peer (p2p) network.
Note: By signing the message, the transaction is protected, so let’s say someone changes the data and tries to transfer the money to different Account C by changing the transfer message, the sign and Msg data will not match, as signature (a hash value) was created with a different Msg data. Whichever node (or peer or computer) receives the message just needs to verify the message using the received message, the sign and the public key of the sender (Person A). Something like this:
isValid(msg, sign, public-key of sender) = true
Step 2: The special nodes (or miners), store the broadcasted Txn in the processing queue. In the cryptocurrency world only the miners are authorized to write to block-chain.
Step 3: The miners collects the bunch of transactions from processing queue and store it in an object called Block (the unit in blockchain). The block also needs to be protected, so that no one can insert any false transaction in the block. A special data-structure called merkle-tree is used to store the transactions belonging to the block. In Merkle-tree each transaction is stored as a leaf node and non-leaf nodes are stored with the hash of its child nodes. As shown below:
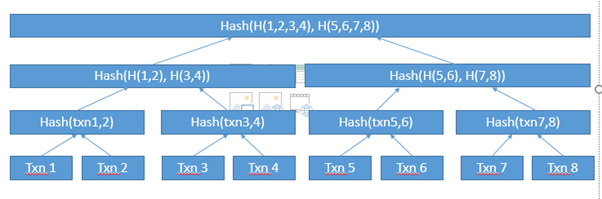
How Merkle tree protects transactions in block: If a false transaction is inserted (or existing transaction is replaced with false one) into already created block, the calculated hash values at the upper nodes will be different then the hash of underlying modified transactions, and miners will simply discard such blocks.
Step 4: The miner also adds additional information on block such as block-id (an incremental number), block-hash, pervious block-hash etc. and signs the entire block-object.
Step 5: Miner is also required to do proof-of-work OR proof-of-stake on the block (called consensus algorithms) before publishing the block on P2P network.
Step 6: Each miner on receiving the completed block, validates the block and on successful validation, adds the block to their local blockchain.
Step 7: Once the transaction entry is done in miner's local blockchain, the transaction is complete. The Person B's wallet will read the nearest's miner's blockchain and the transferred amount will be reflected.
As you can observe that a tempered block published by any malicious miner node will not be accepted by the good miner nodes, and the malicious miner node will very quickly go out of sync with the other miner nodes as the new good blocks will keep getting added to local ledger of the good miner nodes. The only way to add a faulty block to the majority of ledgers is if majority of the miners in the P2P network are malicious. This is called 51% attack.
Types of Blockchain
a. Public blockchain: In such blockchains the data is open to public for viewing. Tools like blockexplorer can be used to view the block data.
b. Private blockchain: The private blockchains are usually created by organizations (or consortium of organizations) to maintain their data privately. These blockchains are usually permissioned.
I would like to end here as I hope this would give reader a decent overview of blockchain as a technology and some of surrounding pieces of infrastructure and how they work together. I have intentionally not detailed out proof-of-work or proof-of-stake concepts and the blockchain forking etc to avoid too much detailing. Do let me know if you want me to cover them in other blogs.
About me: I am an IT professional with 15+ years of experience. Currently working as cloud architect. Also investing my time on BigData and blockchain technologies. Tech learners is my attempt to introduce the technology in simple terms.