
While tracking botnet activity on their honeypot traffic, security researchers at Chinese IT security firm Qihoo 360 Netlab discovered a new variant of Mirai—the well known IoT botnet malware that wreaked havoc last year.
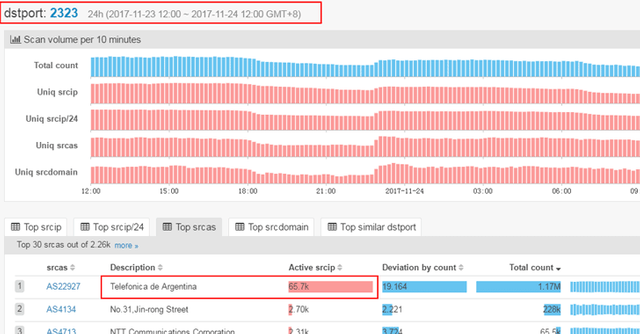
Last week, researchers noticed an increase in traffic scanning ports 2323 and 23 from hundreds of thousands of unique IP addresses from Argentina in less than a day.
The targeted port scans are actively looking for vulnerable internet-connected devices manufactured by ZyXEL Communications using two default telnet credential combinations—admin/CentryL1nk and admin/QwestM0dem—to gain root privileges on the targeted devices.
Researchers believe (instead "quite confident") this ongoing campaign is part of a new Mirai variant that has been upgraded to exploit a newly released vulnerability (identified as CVE-2016-10401) in ZyXEL PK5001Z modems.
"ZyXEL PK5001Z devices have zyad5001 as the su (superuser) password, which makes it easier for remote attackers to obtain root access if a non-root account password is known (or a non-root default account exists within an ISP’s deployment of these devices)," the vulnerability description reads.
Mirai is the same IoT botnet malware that knocked major Internet companies offline last year by launching massive DDoS attacks against Dyndns, crippling some of the world's biggest websites, including Twitter, Netflix, Amazon, Slack, and Spotify.
Mirai-based attacks experienced sudden rise after someone publicly released its source code in October 2016. Currently, there are several variants of the Mirai botnet attacking IoT devices.
The biggest threat of having the source code of any malware in public is that it could allow attackers to upgrade it with newly disclosed exploits according to their needs and targets.
"For an attacker that finds a new IoT vulnerability, it would be easy to incorporate it into the already existing Mirai code, thus releasing a new variant," Dima Beckerman, security researcher at Imperva, told The Hacker News.
"Mirai spread itself using default IoT devices credentials. The new variant adds more devices to this list. Still, we can’t know for sure what other changes were implemented into the code. In the future, we might witness some new attack methods by Mirai variants."
This is not the very first time when the Mirai botnet targeted internet-connected devices manufactured by ZyXEL. Exactly a year before, millions of Zyxel routers were found vulnerable to a critical remote code execution flaw, which was exploited by Mirai.
Secure Your (Easily Hackable) Internet-Connected Devices
Change Default Passwords for your connected devices: If you own any internet-connected device at home or work, change its default credentials. Keep in mind; Mirai malware scans for default settings.
Disable Remote Management through Telnet: Go into your router’s settings and disable remote management protocol, specifically through Telnet, as this is a protocol used to allow one computer to control another from a remote location. It has also been used in previous Mirai attacks.
Check for Software Updates and Patches: Last but not the least—always keep your internet-connected devices and routers up-to-date with the latest firmware updates and patches.
Congratulations @sam4u3! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPDownvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://thehackernews.com/2017/11/mirai-botnet-zyxel.html
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit