What Will I Learn?
- You will learn how to patch bypass admin.
- You will learn how to use PHP filter on your SQL.
- You will learn how hackers work to bypass your admin login page.
- You will learn malicious syntax in SQL.
Requirements
- You must know the use of PHP language.
- You must know SQL.
Difficulty
- Intermediate
Tutorial Contents
Well Hello people, now I wanna teach you how to patch SQLI on your website. Here I just emphasize the bypass admin bug. but first you must know what is SQLI? SQLI (SQL injection) is a hacking technique whereby an attacker can insert SQL commands via url or form form in the website to run database commands. okay now I want to show you how hackers work to bypass your admin login page.
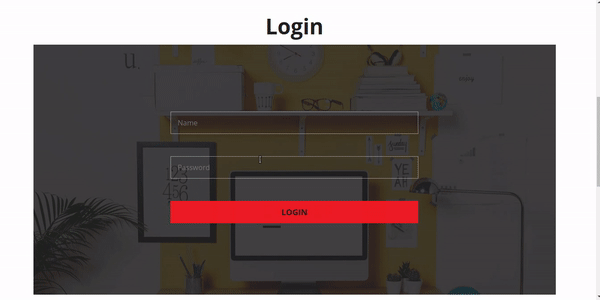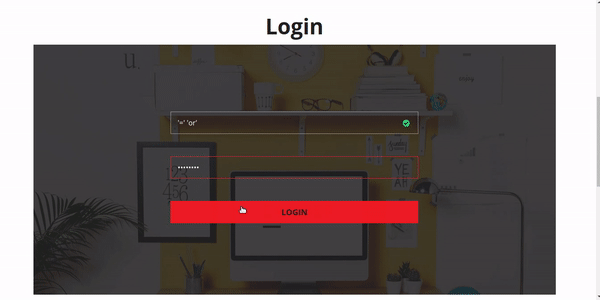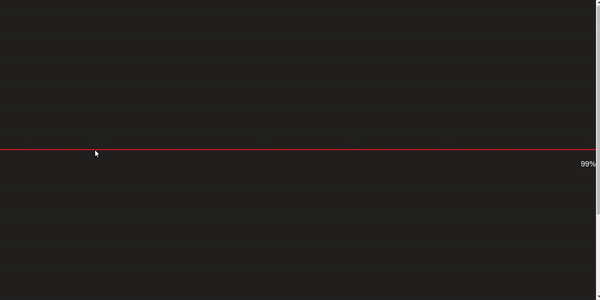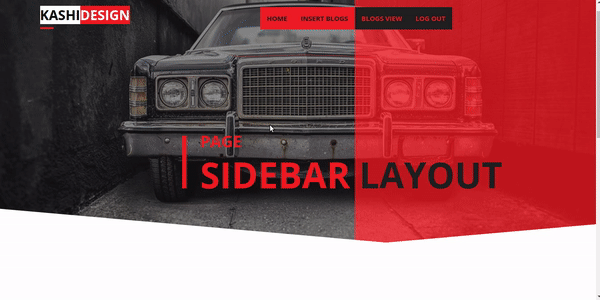
if you saw above you must to be carefully to make a website, now I will tell you some syntax that is considered dangerous and must be removed from your website by filtering it.
'=' 'or'
or 1=1
or 1=1--
or 1=1#
or 1=1/*
admin' --
admin' #
admin'/*
admin' or '1'='1
admin' or '1'='1'--
admin' or '1'='1'#
admin' or '1'='1'/*
admin'or 1=1 or ''='
admin' or 1=1
admin' or 1=1--
admin' or 1=1#
admin' or 1=1/*
admin') or ('1'='1
admin') or ('1'='1'--
admin') or ('1'='1'#
admin') or ('1'='1'/*
admin') or '1'='1
admin') or '1'='1'--
admin') or '1'='1'#
admin') or '1'='1'/*
How to patch this bug?
here I have a source code that is vulnerable to this bug
<?php
include'connection.php';
if (isset($_POST['login']))
{
$name=$_POST['name'];
$password=$_POST['password'];
$query="SELECT * FROM admin where admin_name='$name' AND admin_password='$password'";
$rq=mysqli_query($conn,$query);
if (mysqli_num_rows($rq) > 0) {
$id=0;
@session_start();
$_SESSION['admin_name']=$name;
$_SESSION['user']=$id;
echo "<script>
alert('Logged in');
window.location.href='index.php';
</script>";
}
else
{
echo "<script>
alert('Email or Password is inavlid');
window.location.href='login.php';
</script>"
}
}
?>
you can see on that source without PHP filter, the PHP filter that should be used is addslashes () function. The addslashes () function is a string function to give a slash or slash if there are certain characters in the string. The characters are: Single Quote ('); Double Quote ("); backslash (). You can see again at above where syntax that is considered dangerous using Single Quote ('); Double Quote ("); backslash (), so this function very important to your website right?. We can put addslashes to that source in part
$name=$_POST['name'];
$password=$_POST['password'];
and you can add addslashes() function like this
$name=addslashes($_POST['name']);
$password=addslashes($_POST['password']);
if you already to put addslashes() function Like that I promise your website now don't have that bug again :)
see the picture below I have patched BYPASS ADMIN bug on my website
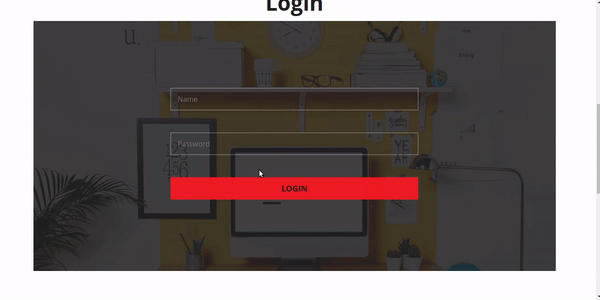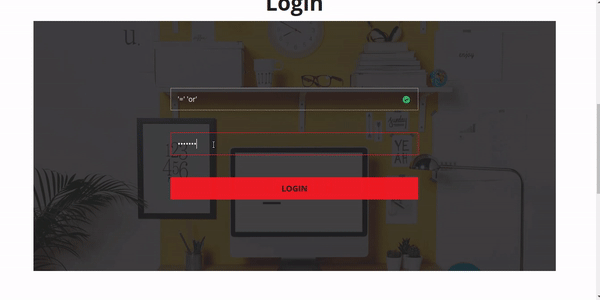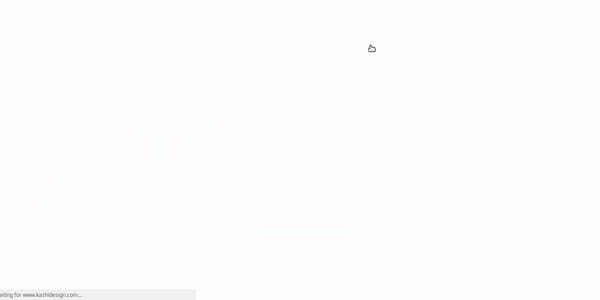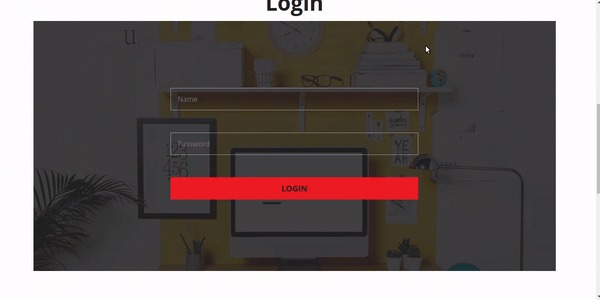
okay until here i teach you How To Patch SQLI on Your Website: Bypass Admin. Cheerio!
Posted on Utopian.io - Rewarding Open Source Contributors
Thank you for the contribution. It has been approved.
You can contact us on Discord.
[utopian-moderator]
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hey @farahulfa I am @utopian-io. I have just upvoted you!
Achievements
Suggestions
Get Noticed!
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit