Understanding of Phishing
Phishing is a method that hackers use to steal passwords by tricking targets using a fake login form on a fake site that resembles the original site.
in some cases, the fake site is not very similar but because the target is less careful and have no experience about phishing methods then it could be trapped.
How Phishing works
In a way the hacker makes us click on their fake site links, with an interesting image on social media, persuasion on email and so on.
After clicking, we will be directed to a fake site which on the site there is a form field eg facebook login form with a word that convinces that our facebook has logout and ask us to enter username and password again. we do not think that the site is just a clone will fill in the username and password without suspicion.
What we put into the form field will be stored on the server the hacker. So we still have time to change our password before the hacker sees our username and password on the server.
Our account will be taken over. the hacker is likely to use our account to spread the psihing url to our friends to get more victims.
Hacking passwords with phishing methods is the easiest to practice, that's why there are so many cyberspace scattered referrals address addresses that redirect our browsers to pishing web addresses or fake webs.
How to prevent phising
To prevent the occurrence of phishing there beberpa tips that you can follow as described below.
When you go to a site, pay close attention to your use of a domain name whether using an official or fake address.
Never click url carelessly, especially on illegal sites.
Shop only on trusted sites, and online shop owners that you know have integrity. Online shopping is often made as a container for minipu.
When you use a public computer, do not leave the computer before logging out, especially your login to important sites, and delete all history in the browser.
Do not believe in suspicious emails that are often sent periodically to your email address.
Turn on firewall features to block suspected sites as illegal sites. The firewall itself can be said as a dividing wall that will let something into the komptuer if it deems good, and when suspected to be immediately in the block.
Finally remain cautious and sensitive to crime on the internet is growing and rampant happen.
below is a tutorial to do web phishing on linux using SET application (Social-Engineer Toolkit)
The Social-Engineer Toolkit is an open-source penetration testing framework designed for Social-Engineering. SET has a number of custom attack vectors that allow you to make a believable attack in a fraction of the time.
here are the steps to create web phising with setollkit
select on Applications >>> Exploitation Tools >>> Social-Engineer Toolkit (SET), or type in your terminal "setoolkit"
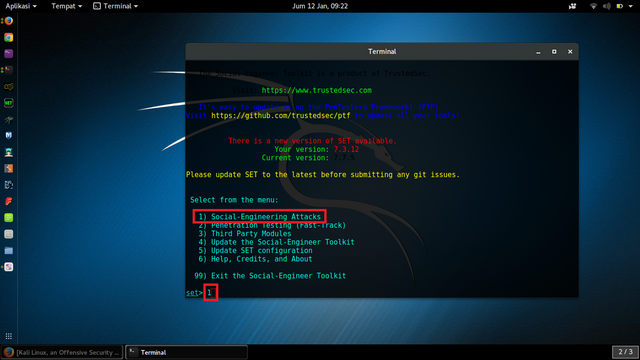
Select from the menu: [SELECT 1) Social-Engineering Attacks
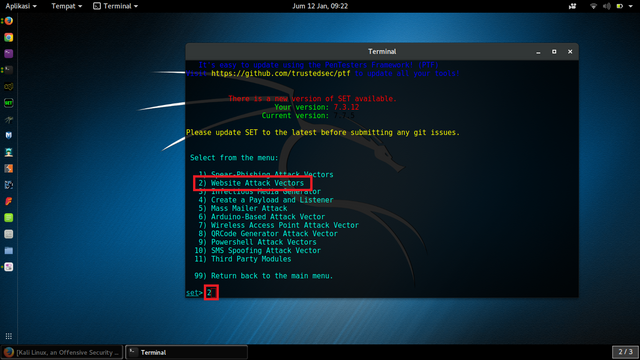
Select from the menu: [SELECT 2) Website Attack Vectors
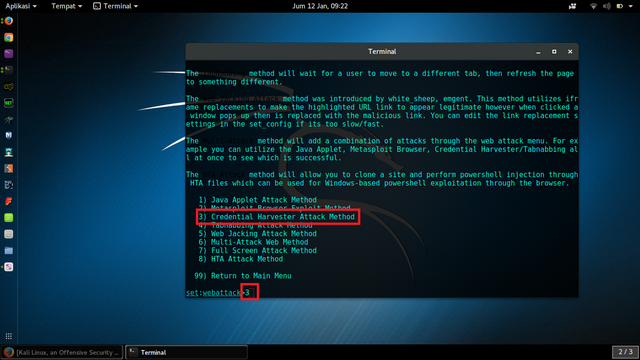
[SELECT 3} Credential Harvester Attack Method]
(SELECT 2) Site Cloner
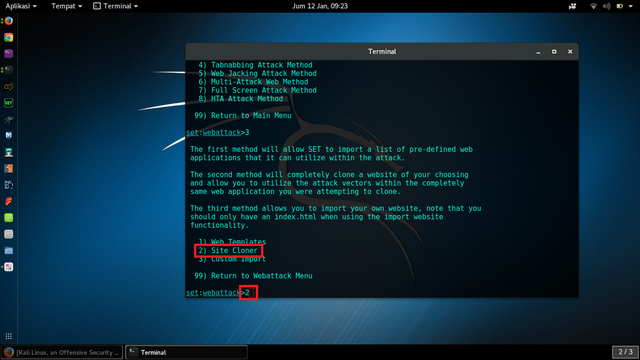
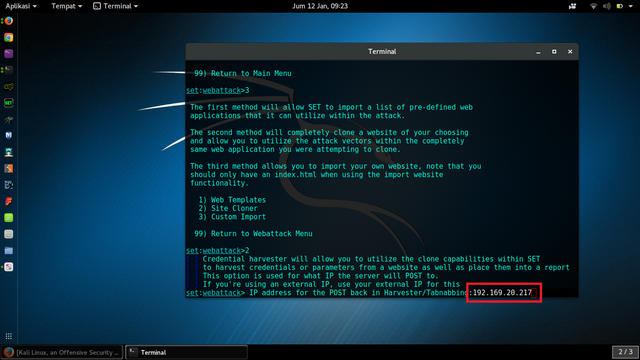
enter the local computer's ip address
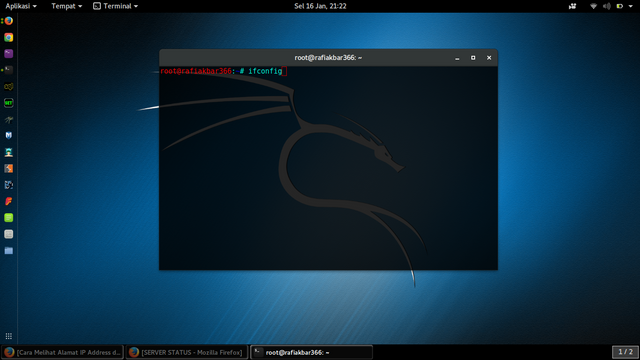
to see the local ip address of our computer, open a new terminal and type "ifconfig"
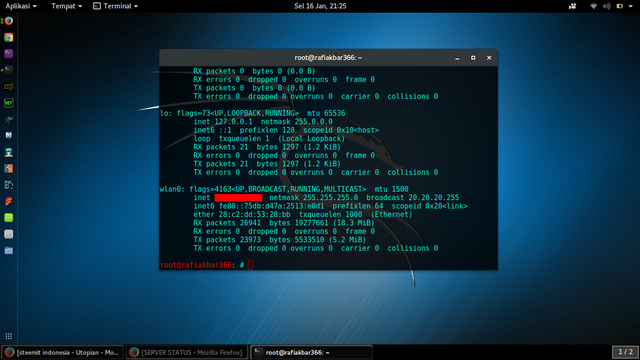
block and copy the ip address by pressing SHIFT + CTRL + C
paste in setoolkit by pressing SHIFT + CTRL + V

Enter the url to clone: [Choose your target to be clone website]
example: https://www.facebook.com/
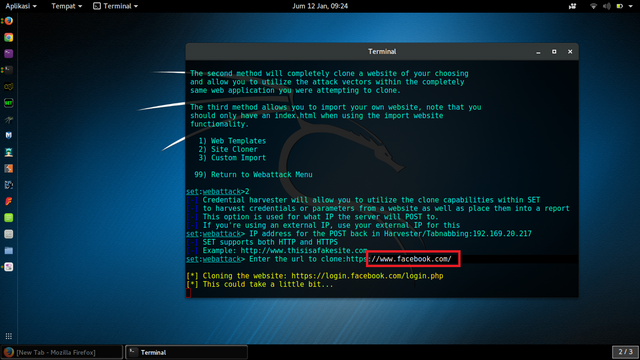
Press ENTER and type y
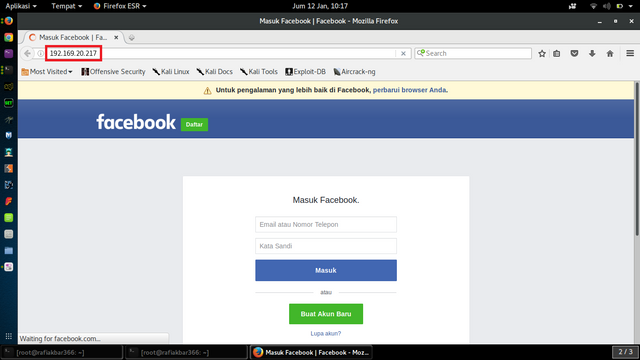
if victim access our local IP in browser, will appear fake facebook login page which we have created earlier. look at the picture below
to see the local ip address of our computer, open terminal then type "ifconfig"
Wait until the victim enters the username & password into the cloner's website
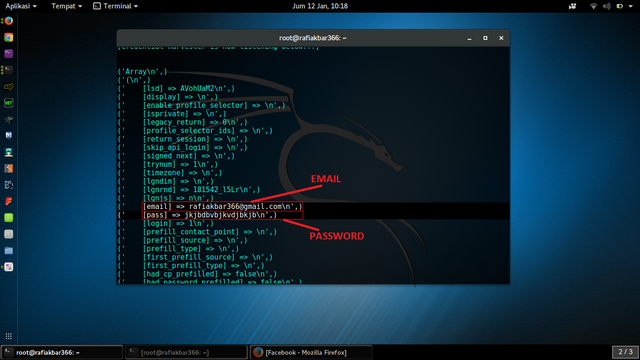
or can be accessed in the VAR / WWW / HTML directory
this only applies in the same network
Posted on Utopian.io - Rewarding Open Source Contributors
Wow Rafia some great detail there, Im blown away by your intelligence. If you like photography, take a look at my posts. Let me know what you think Hun
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
thank you very much for having seen my article, i will repay your kindness
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Your contribution cannot be approved because it does not follow the Utopian Rules.
Phishing is highly illegal . That type of content is not welcome on Utopian (as well as social engineering as a whole as long as it falls under Fraud or breaks the law in any other way)
You can contact us on Discord.
[utopian-moderator]
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I'm sorry, I did not know before, I'm really sorry
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit