Disclaimer: I take no responsibility for & cannot warrant patching resources supplied by Microsoft, and assume no liability or responsibility for any systems or data that may be affected, nor am I offering or liable to provide individualised advice or assistance, I am simply sharing these resources and synopsis with the steemit community members for their own use and consideration as they see fit.
TLDR
I'm concerned by the nonchalance I've seen towards this pair of threats in my recent inter-site travels while executing my routine functions, the ostensible reason being that the threat has passed or is non-existent. The truth is that not only are both these threats are still active, but that they also use additional methods not addressed by the patches to spread from a compromised system to other systems in the local network, even if those systems have been patched.
Which is why it's imperative to ensure that all Windows systems that are currently connected or may become connected to your network are patched against these threats.
What's more insidious is that ExPetr (the recent Petya variant) portrays itself as a cryptolocker ransomware but is in fact destructive, meaning there's no coming back once the damage is done, even if you pay the ransom.
Look for your Windows OS below below, if it's not listed then Microsoft haven't released a patch for it. More detailed information and some history is in the Synopsis section.
Supported Windows systems:
Windows Vista & later, including Windows 8.1 but not Windows 8, are offered applicable mitigation patches via Windows Update:
- Open Windows Update (via Control Panel or type update in the Start Menu search box)
- Click Check for updates
- Select & install all updates marked as Critical or Important
- Reboot if necessary
Unsupported Windows systems:
XP, NT, Windows 2000, Server 2003, Windows 8, patches are available but will not be offered via Windows Update, however they are available from Microsoft for manual download & install:
- Windows XP SP3 x86
- Windows XP SP2 x64
- Windows XP Embedded SP3 x86
- Windows Server 2003 SP2 x86
- Windows Server 2003 SP2 x64
- Windows 8 x86
- Windows 8 x64
Further Microsoft Security Bulletin MS17-010 resources for guidance & verification:
- Unsupported Windows systems: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
- Supported Windows systems: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Synopsis
WannaCry
Utilising the NSA exploit EternalBlue to attack systems worldwide, in it's first few days it quickly and successfully affected a fair number of systems from hospitals to government and even some Victorian speed camera systems. Once 'patient zero' in a given network is compromised it then spreads to and afflicts neighbouring networked systems. Microsoft released patches in March for these vulnerabilities, but any systems not kept up to date remain vulnerable to the exploit. Soon after the initial impacts a built-in kill switch was discovered and data recovery/decryption processes started appearing.
Petya/ExPetr
A new variant of an earlier ransomware known as Petya has surfaced in the last few days using a modified version NSA EternalBlue and EternalRomance exploits. Unlike WannaCry, which uses EternalBlue to spread rapidly across the internet and local networks, this attack also uses two Windows utilities (PSExec & WMIC) to move laterally on local networks, allowing it to infect machines patched against the vulnerabilities exploited by EternalBlue, adding layers of complexity to this attack..
Once present on a compromised system it overwrites the Master File Table and Master Boot Record, preventing normal bootup & system operation:

One organization reports that one unpatched machine was the culprit at its location, adding that it lost PCs due to a corrupted MBR, while other machines were showing the ransom note:
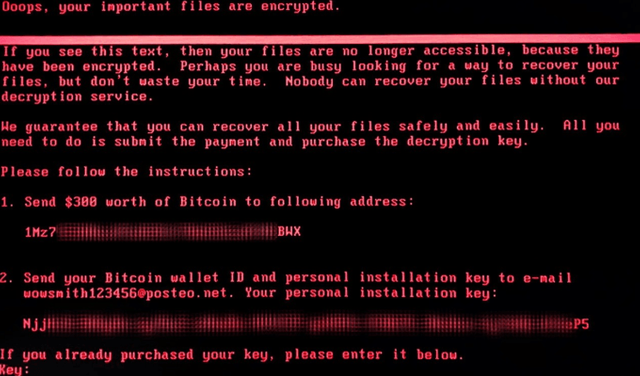
Researchers at Kaspersky Lab have discovered an error in the ExPetr ransomware code that prevents recovery of lost data, apparently there's ‘Little Hope’ to Recover Data Lost to Petya Ransomware.
Unlike WannaCry, this new ransomware sample contains no killswitch and is burrowing through corporate networks and endpoints, forcing workers at a number of locations to pull their machines from the internet.
Since the attack began critical industries and services have been affected in Russia, Ukraine and then throughout Europe, including the radiation monitoring station for the crippled Chernobyl nuclear power plant and pharmaceutical giant Merck and Co.’s MSD operation in the United Kingdom. This augments a growing list of victims that also includes Danish shipping giants Maersk, Ukraine’s central bank, the country’s Borispol Airport in Kiev and dozens of other victims there, along with SaintGobain, a leading manufacturer in France and Russian oil company Rosneft and steel manufacturer Evraz.
Researcher Matt Suiche of Comae Technologies said the malware is more wiper than ransomware, akin to Shamoon, the wiper malware behind the attacks on Saudi Arabia’s Aramco oil company. Suiche said this malware destroys the first 25 sector blocks of a hard disk, and the MBR section of the disk is purposely overwritten with a new bootloader.
“The ransomware was a lure for the media, this version of Petya actually wipes the first sectors of the disk like we have seen with malwares such as Shamoon,” Suiche wrote in an analysis published today. “The goal of a wiper is to destroy and damage. The goal of a ransomware is to make money. Different intent. Different motive. Different narrative.”
Victims, meanwhile, continue to make payments in a futile attempt to recovery their lost hardware and data. German host Posteo said yesterday that it shut down the attacker’s email account, [email protected], which prevents victims from contacting the entity behind the attack in order to send them their Bitcoin wallet address and infection ID in order to verify payment of the $300 ransom.
The author of the original Petya malware has release the encryption keys, but they are of little use to systems afflicted by ExPetr due to the non-recoverability of its destructive processes.
So please, consider that promiscuous unprotected solicitation in any form, whether visceral or virtual, can leave you with unwanted but lasting affliction.
And remember: Internet Street is not Sesame Street.
nice post
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
thank you@astaetram, I hope it is useful to you.Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit