Having a Wi-Fi network in your home is almost mandatory these days, with so many mobile phones, tablets, laptops, video games, TVs and other connected devices. At the same time, there is always the possibility that some smart guy has taken advantage of a minimal gap that you have left in time to create your network and be connected to it without your permission.
There are several ways you can accomplish this task; the most basic of all is to look at the LEDs of your router to see if it is blinking more than normal. This will not work, however, if you have many devices connected to your network, since you probably will not identify any difference. Also there is not much that can be done to solve the problem by this method.
Otherwise, more refined, it is to access the settings of your router. Any model, however simple it may be, will show a list of all currently active connections, allowing the blocking of any strange activity. Unfortunately, each router has its own interface, with unique menus, then it is impossible to detail how to access this option (it is recommended to look at the manual) but you need to access the settings, usually available at http://192.168.0.1.
The last option, but no less useful, is to use a program to identify strange connections. One is the SoftPerfect Network Scanner, but there are several other similar. The software makes a list of all the IPs and connected devices on your network. He is even able to turn off a connected computer.
Just follow the step by step below to see the list of connected devices. If you have, for example, six devices connected to your home, but the list shows connections 9, for example, there is something wrong.
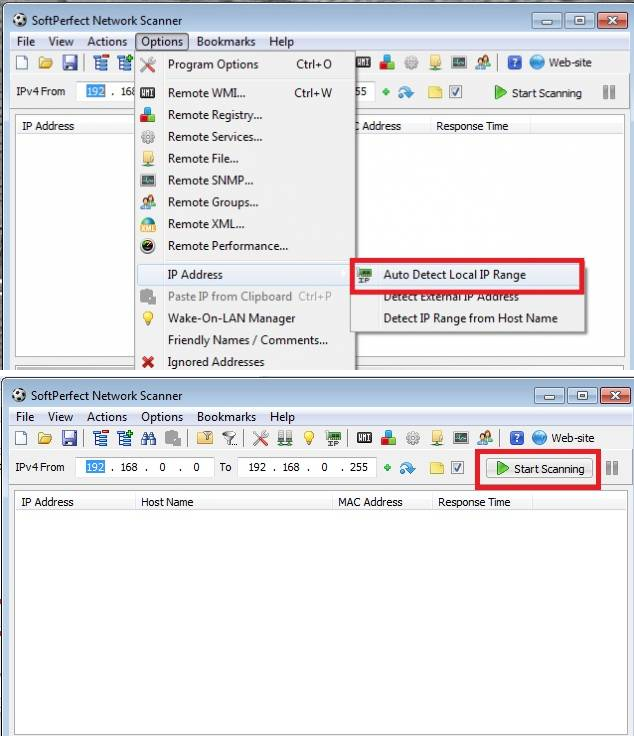
How to create a secure network and avoiding strange connections:
The simplest way to solve this problem is to reset the router and change your settings to make sure this does not happen again. The lower line steps do not fully guarantee the security of your connection, but are very helpful and are an added layer of difficulty to possible attacks or signal thieves:
Change the network name (SSID) and password: when installing the device at home, it must immediately change the network name and password. Without it, the device will use a default name factory without password, which facilitates the discovery of a possible model cybercriminal. With this information, it can exploit the vulnerabilities that are already known.
WPA2 Encryption: As stated before, the least you should do is put a password (very strong preference). After that, another important step is to set the standard for safety. WPA or WPA2 (prefer the second option if possible) are much safer than WEP protocol, which can be broken easily.
Disable WPS (WiFi Protected Setup): The feature can manage security more simply, but is vulnerable. Within hours, the PIN 8 numbers can be broken by a brute-force attack, leaving the exposed network.
Enable MAC filter: Using this tool, only authorized devices can connect to the network. Each device has its own network adapter, identified by an address containing a unique string of letters and numbers. When entering this information into the router, only registered addresses in the access list can connect.
Disable display of the network name (SSID): By doing so, your network is "invisible" to others, making it difficult directing the attacks. The problem is that you need to enter the network name manually for each new device that plugs.
Set password to modify settings: In addition to the network access password, it is important to create another to move the router itself. Usually the equipment comes with a default password or even no password, creating a serious gap. If any cybercriminal get into your network, it can change the router to direct the user to malicious sites that mimic legitimate pages, among many other alternatives.
Firmware Update: Doing so should resolve critical security bugs and widely known. In the technology industry, in general, outdated software means more loopholes, so the tip goes for all your devices.