Yes, we can validate the Wikileaks emails via DKIM - Many have repeatedly claimed that some of these emails are fake or have been modified, that there's no way to validate each and every one of them as being true. Actually, there is, using a mechanism called DKIM.
DKIM is a system designed to stop spam. It works by verifying the sender of the email. Moreover, as a side effect, it verifies that the email has not been altered.
Another question is whether DKIM could be forged if the email server is compromised. At the end of the day anything's possible, but I believe both the sending and receiving server domain private keys would have to be compromised to pull that off. And in this case, the Podesta emails were from google GMail, which is very unlikely to have been a server-level hack.
Full story: http://blog.erratasec.com/2016/10/yes-we-can-validate-wikileaks-emails.html
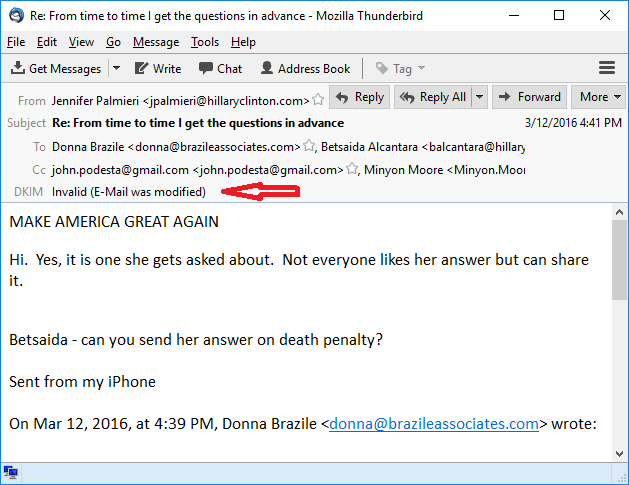
Apparently there are some emails failing DKIM , I've been watching a few private chats where people have been working on checking the full set.
Heres an sqlite db with the results of the checks so far with a warning from its creator
https://mega.nz/#!n9FBXRya!xYXqlsX0QkMQZiGLZ3qZ26d5hF05iZseg6jJjgd-uDk
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit