
After nearly a 2 month break, Wikileaks is back with more from their CIA document archive. Dubbed Vault 8, this series of publications focus on previously unseen source code and gives a retrospective analysis of previously published CIA malware hacking tools. Wikileaks states in their press release that, similarly to Vault 7, Vault 8 will not reveal any zero-days or other vulnerabilities that could be 're-purposed by others'.
Source code and analysis for CIA software projects including those described in the Vault7 series. This publication will enable investigative journalists, forensic experts and the general public to better identify and understand covert CIA infrastructure components.
Below is a screenshot of the source code repository:
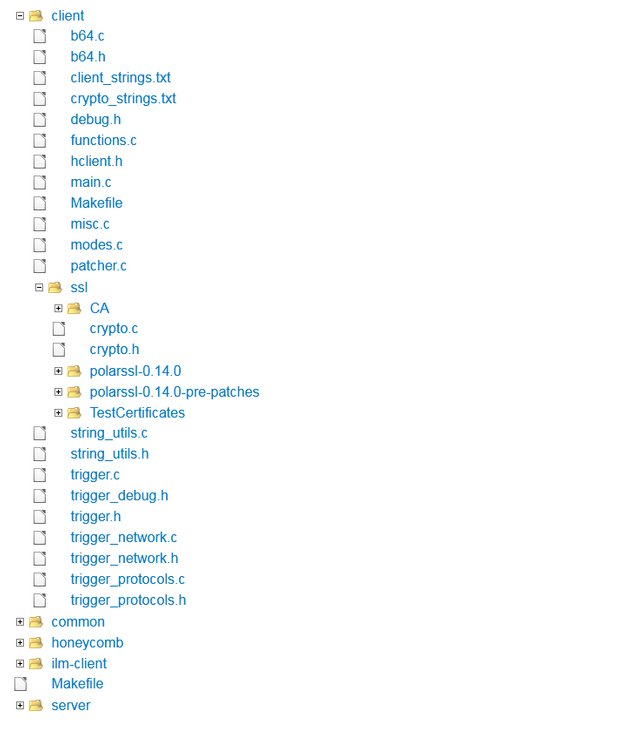
The first analysis to be carried out by Wikileaks in this Vault 8 series was done on a CIA project called Hive. Wikileaks originally published documents exposing Project Hive in April. This revealed the CIA's elaborate malware command and control infrastructure developed to manage a suite of custom exploits used to hack, control, record, and exfiltrate data from target systems.
Today, April 14th 2017, WikiLeaks publishes six documents from the CIA's HIVE project created by its "Embedded Development Branch" (EDB). HIVE is a back-end infrastructure malware with a public-facing HTTPS interface which is used by CIA implants to transfer exfiltrated information from target machines to the CIA and to receive commands from its operators to execute specific tasks on the targets. HIVE is used across multiple malware implants and CIA operations. The public HTTPS interface utilizes unsuspicious-looking cover domains to hide its presence.
According to a 2015 User Guide Hive has two main functions - a beacon and an interactive shell. Which are both designed to provide an initial foothold for deploying further 'full featured tools'.
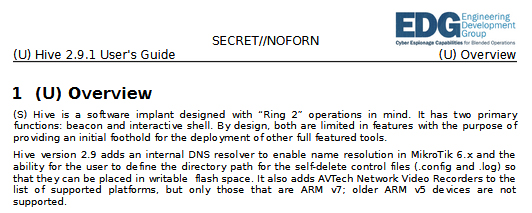
Once the selected malware has been successfully deployed to a target machine it will then use Hive to communicate via HTTPS with a web-server of a cover domain. Each cover domain is connected to an IP address of a commercial VPS (Virtual Private Server) provider such as Amazon. This then forwards all incoming traffic to a CIA controlled server called 'Blot'.
The redirected traffic is then checked for a valid beacon. If one is found it will forward the redirected traffic to a tool handler, known as Honeycomb, where the CIA can then save the stolen data or initiate further commands on the target machine.
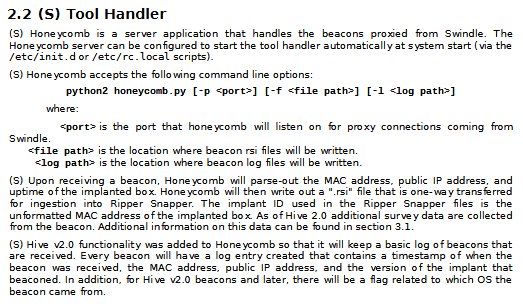
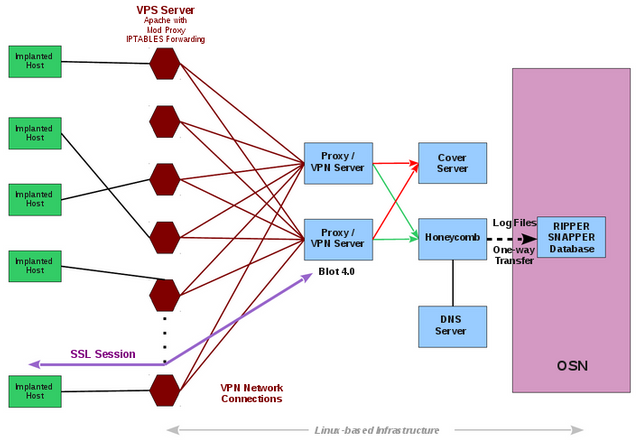
The Analysis
To allow this communication to go undetected over HTTPS the CIA needed a valid SSL certificate. This recent Vault 8 analysis by Wikileaks reveals that the CIA were able to falsify Kaspersky Lab SSL certificates allowing them to covertly communicate with multiple implants via the Hive infrastructure. Disguising this communication as legitimate traffic gave them the ability to securely transfer data and commands without ever being detected by anti-virus software or other security protocols.
SSL stands for Secure Sockets Layer, a global standard security technology that enables encrypted communication between a web browser and a web server. It is utilized by millions1 of online businesses and individuals to decrease the risk of sensitive information (e.g., credit card numbers, usernames, passwords, emails, etc.) from being stolen or tampered with by hackers and identity thieves. In essence, SSL allows for a private “conversation” just between the two intended parties. To create this secure connection, an SSL certificate (also referred to as a “digital certificate”) is installed on a web server and serves two functions:
- It authenticates the identity of the website (this guarantees visitors that they’re not on a bogus site)
- It encrypts the data that’s being transmitted
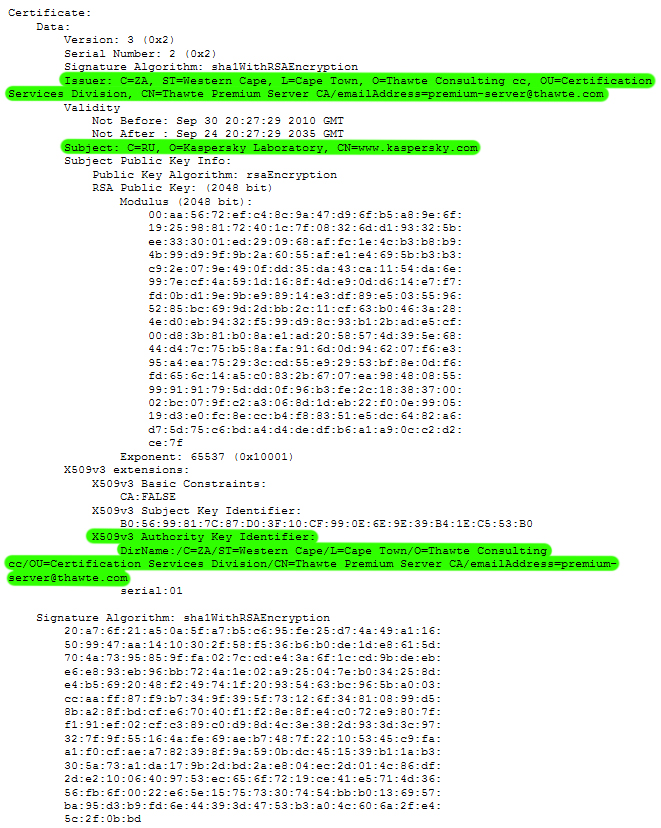
The certificate authority the CIA were able to create fake SLL certificates for was a South African company called Thawte. Thawte advertises themselves as a 'leading global certificate authority' that provides SLL certificates and online security, through 'robust authentication practices', to millions of web users around the world.
(At time of writing there still hasn't been any official statement made by the affected SLL certificate company, Thawtes.)
US intelligence officials have repeatedly accused Kaspersky Lab of being involved in the alleged Russian state-sponsored hacking of the US election. Back in September the Department of Homeland Security even put out a warning to all governmental agencies advising them to stop using Kaspersky products within 90 days.
DHS Statement on the Issuance of Binding Operational Directive 17-01 | DHS.gov - 09/13/2017
WASHINGTON – After careful consideration of available information and consultation with interagency partners, Acting Secretary of Homeland Security Elaine Duke today issued a Binding Operational Directive (BOD) directing Federal Executive Branch departments and agencies to take actions related to the use or presence of information security products, solutions, and services supplied directly or indirectly by AO Kaspersky Lab or related entities.
Kaspersky immediately put out a statement denying any 'inappropriate' ties with the Russian government, or indeed any involvement in the alleged hacking of the 2016 US presidential campaign.
Kaspersky Lab Response to Issuance of DHS Binding Operational Directive 17-01 | Kaspersky - 09/13/2017
Given that Kaspersky Lab doesn’t have inappropriate ties with any government, the company is disappointed with the decision by the U.S. Department of Homeland Security (DHS), but also is grateful for the opportunity to provide additional information to the agency in order to confirm that these allegations are completely unfounded.
To combat this damaging and xenophobic witch-hunt conducted by the US, Moscow-based Kaspersky Lab has recently launched a transparency initiative which allows independent groups and third parties to review their source code and business practices in a hope it reassures the infosec community it's done nothing wrong.
Kaspersky Lab announces comprehensive transparency initiative | Kaspersky Labs - 10/23/2017

- INDEPENDENT SOURCE CODE REVIEW
To start by Q1 2018, undertaken with an internationally recognized authority- INDEPENDENT REVIEW OF INTERNAL PROCESS
To verify integrity of our solutions and processes- THREE TRANSPARENCY CENTERS WORLDWIDE IN THREE YEARS
Enabling clients, government bodies & concerned organizations to review source code, update code and threat detection rules.
First center in 2018, 3 centers by 2020, in Asia, Europe and the U.S.- INCREASED BUG BOUNTY REWARDS
Up to $100K per discovered vulnerability in main Kaspersky Lab products
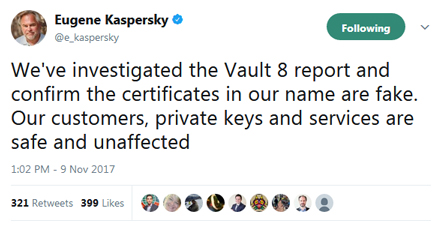
Finally Eugene Kaspersky, head of Kaspersky Labs, made a brief statement yesterday on Twitter acknowledging the recent news by confirming the forged SLL certificates were indeed fake. He also went on to assure existing customers their private keys and services are unaffected.

What I'm taking from all these releases from wikileaks is that even if, and I mean IF the Russian government helped Trump get elected can it ever truly be proved due to all the sinister tools available to the CIA etc. Keep up the great work reporting on these leaks.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks. This is a good question. I would like to think that now digital forensic experts know the truth they wold be able to factor these sinister obscurification tools into their analysis.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Mr. Fortified, pleasant surprise to find another one of your excellent posts!
I think that it was a necessary move by Kaspersky to show their source code to assure people of transparency and good faith. Yet again, the CIA is showing that they will stop at nothing to achieve their dubious goals framing Kaspersky labs. This also provides real evidence that the US Intel comm. regularly uses their spyware arsenal to leave false fingerprints and misdirect investigations towards other parties. Russia, Russia, Russia.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hey V. Thanks
Yes I believe Kaspersky weren't left with any choice at the end of the day. I hope it starts a transparency revolution. Maybe it'd be a good marketing move for tech companies to provide proof that they aren't compromised by the CIA.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Disclaimer: I am just a bot trying to be helpful.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Its So technical . Everything bounced above my head .
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit