Content
Assuming that A and B cannot trust each other, then a third party that can be trusted by both A and B is introduced to act as a notary as an intermediary. In this case, A and B can indirectly trust each other.
Insert picture description here
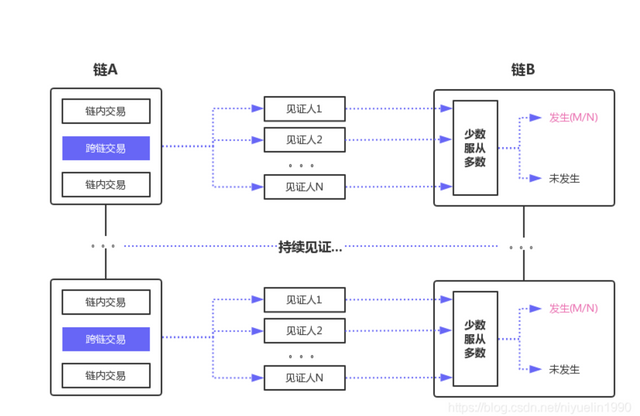
Witnesses continuously collect data, and also perform transaction confirmation and verification. The witness at this time will become a trusted third party, which can be a trusted centralized witness mechanism for both parties, or a group of decentralized nodes. After the witnesses continue to collect and verify the data of chain A, chain B obtains chain A in a certain proportion of transactions. In layman's terms: a trusted third party tells B chain A what happened on chain, or tell B the truth of a certain message.
Single-signature notary public mechanism: The single-signature notary public mechanism is also called a centralized notary public mechanism, which is usually acted by a single designated independent node or institution. Method: Users can uniformly transfer funds to the account of a notary, and there is a notary to exchange assets across the chain.
Multi-signature notary mechanism: The multi-signature notary mechanism can complete cross-chain transactions only after multiple notaries jointly sign on their respective ledgers and reach a consensus. Each node of the multi-signature notary group has its own key, and only when a certain number or proportion of notary signatures is reached, the cross-chain transaction can be confirmed. Compared with the single-signature mode, this method has higher security. A few notaries who are attacked or committed evil will not affect the normal operation of the system. However, this method requires the two chains to have the function of supporting multi-signature.
Distributed signature notary mechanism: The system has and only generates one key, and no one in the notary group will have the complete key. The key is randomly sent to each notary node in the form of fragments, and Fragments are processed ciphertexts, so even if all notaries put the fragments together, they cannot know the complete key, which fully guarantees the security of the key.