
EXPLAIN WHAT DOES THE RESISTANCE TO COLLISION MEAN AND WHAT DOES RESISTANCE TO PREIMAGE MEAN

INTRODUCTION
The need for encrypting and protection of data from any third-party peers is required in the cryptocurrency market transactions and to this effect, the introduction of cryptography through hashing has made it possible that data or information can only be passed through a receiver and a sender without the intersaction of any third-parties along with it data sent to them privately.
Because of the irrevocable structure of hashing under cryptography, data can be delivered with an assured security, authorisation and authentication of a data between two nodes, this methods has been effective mostly when it come to the issue of securing cryptocurrency transactions in the market.
RESISTANCE TO COLLISION
The word Collision can be referred to as a direct or forceful contact that occurs between two or more things while the word Resistance is an act of refusal or unwillingness to something. Therefore, Under Hash functions, in a simpler terms, this is an act or process of refusal of a particular or more inputs when collide with another to fabricate the same input.
Cryptography has a hash function security that was first published in 2001 which is Secure Hash Algorithm 256-bit (SHA-2) with the use of that medium, a infinitesimal or slim chance of generating a same input has been recorded, it's only an output of 160bit length can be predicted to collide if possible.broken. Just like some mathematical calculations which are hard to find it solutions same with the resistance to collision.
But with the new technique Message-digest algorithm (MD5) that comes with a value of 128-bit and Secure Hash Algorithm (SHA-1) with a value of 160-bit has made it more methodical in finding collisions in the system.
RESISTANCE TO PREIMAGE
This hash function property Intensely focuses on a one-part way function (Forward) under this, Once an input hashed is generated it cannot generate an output because of it structure, this function indicates that this medium is builded on a high secured fence in hashing without a return.
This perimage has a second preimage which both makes me it impossible for perpetrator to find a hash under it functions although this has a similarities with the resistance mentioned above.

USE TRONSCAN AND ETHERSCAN TO VERIFY THE HASH OF THE LAST BLOCK AND THE HASH OF THAT TRANSACTION (SCREENSHOT IS REQUIRED FOR CHECKING)

TRONSCAN PROCESS
1: Open your browser and search by filling in https://tronscan.org/#/, it will open and below image shows its first appearance.
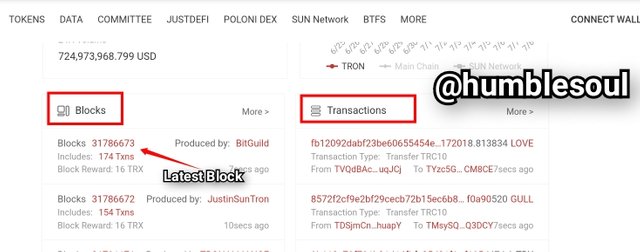
- From the image above, You can see the lastest block as of when viewed was: 31786673 and the list of lastest transactions made.
2: Click on the lastest block to view more details of it procession.
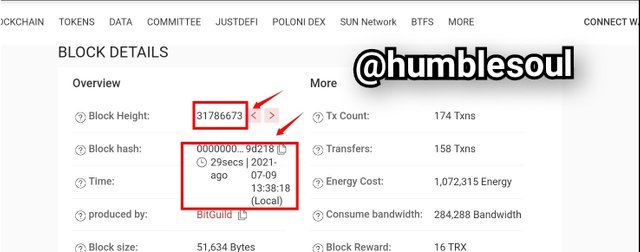
From the details above, you see the following:
- Block Height: 31786673
- BlockHash:0000000001e506b1246be5f377796ed50dfbd5b1db5c087c73ed26fd2699d218
- Block Size: 51,634 bytes
Along with other necessary data required for the transaction.
3: On the block page, to verify the hash, scroll down to the 'TRANSACTIONS SECTION' to view the latest transactions on the blockchain as you can see from the image below.
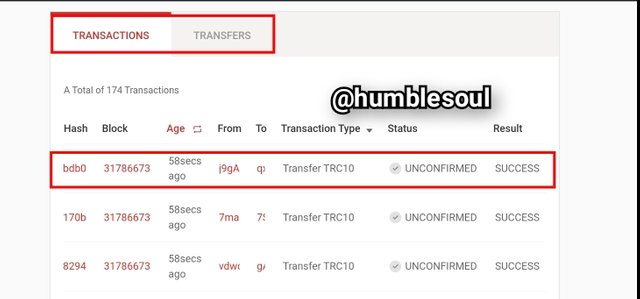
4: Click on the lastest block to view clearly in details the blockchain details.
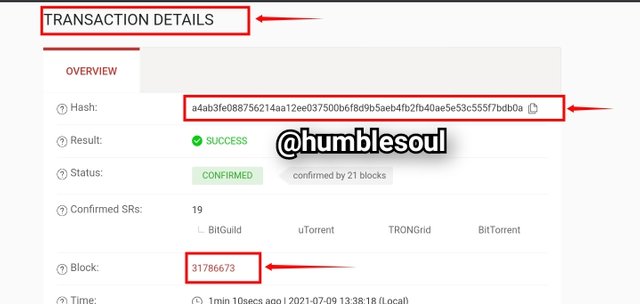
- From the image above, you can see the lastest transactions hash which was: a4ab3fe088756214aa12ee037500b6f8d9b5aeb4fb2fb40ae5e53c555f7bdb0a
ETHERSCAN PROCESS
1: Open your browser and search by filling in https://etherscan.io/ it will open and below image shows its first appearance
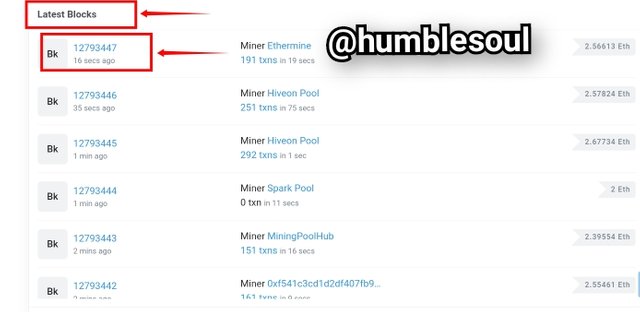
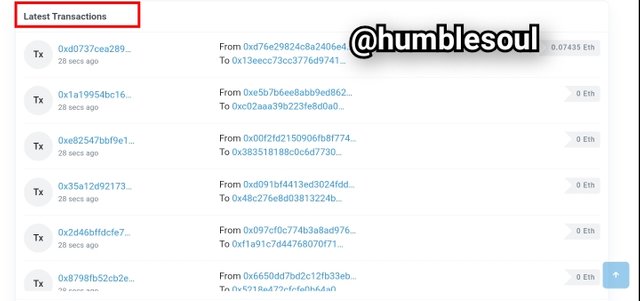
- From the image above you can see the lastest block along with the transactions sections by the left-side of the image.
2:Click on the latest block above and the imagebelow shows the full details of the transaction under that particular block
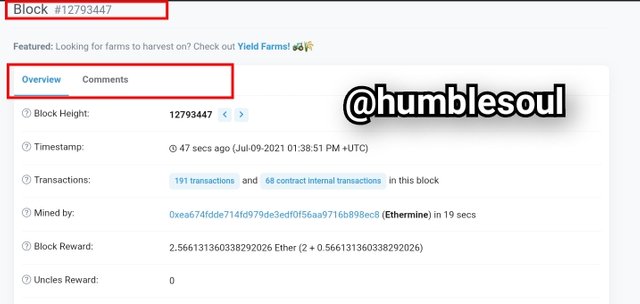
- Based on the image above, to view the block hash, scroll down the page.
3: Below image shows the hash of the latest block as of the time viewed.
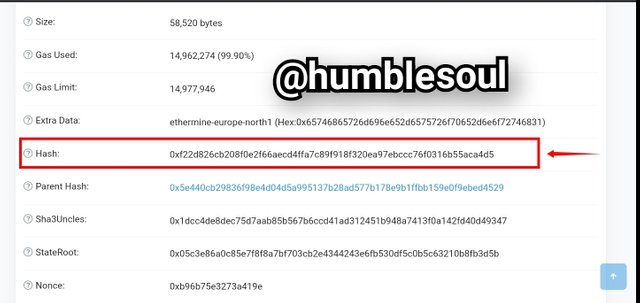
- From the image above: The hash was:0xf22d826cb208f0e2f66aecd4ffa7c89f918f320ea97ebccc76f0316b55aca4d5
4: To search the latest transactions on the block, scroll up on the same web-page and click on the TRANSACTIONS ROW (191 Transactions)
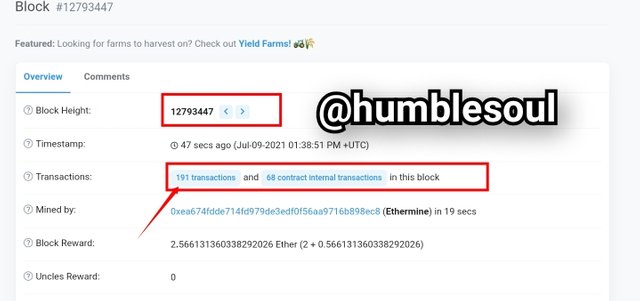
5: Following the previous procedure, the image below will display, continue by clicking on the latest transactions below
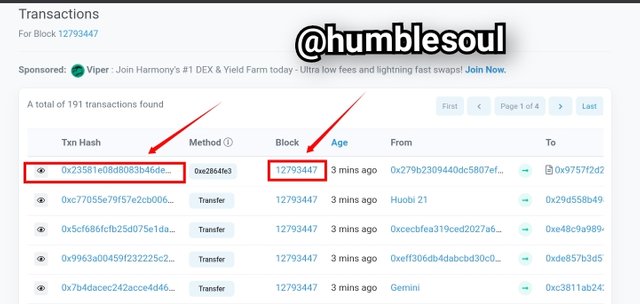
6: After clicking on the transactions, the image below appears
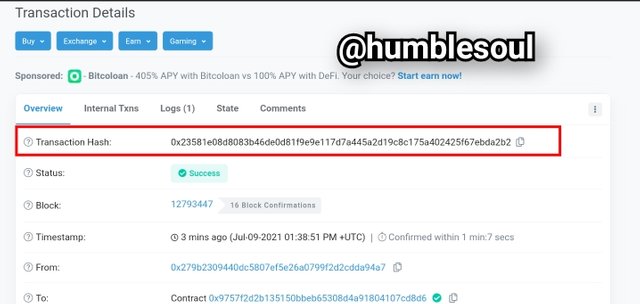
- Based on the image above, the lastest hash transaction as of the time viewed was:0x23581e08d8083b46de0d81f9e9e117d7a445a2d19c8c175a402425f67ebda2b2
THAT'S THE END OF THE PROCEDURE

GENERATE THE HASH USING SHA-256 , FROM THE WORD CRYPTOACADEMY AND FROM Cryptoacademy. SCREENSHOT REQUIRED. DO YOU SEE ANY DIFFERENCE BETWEEN THE TWO WORDS? EXPLAIN

HERE IS MY PROCESS
1: Use the link provide and fill in your browser search https://passwordsgenerator.net/sha256-hash-generator/ and image below will loadup.
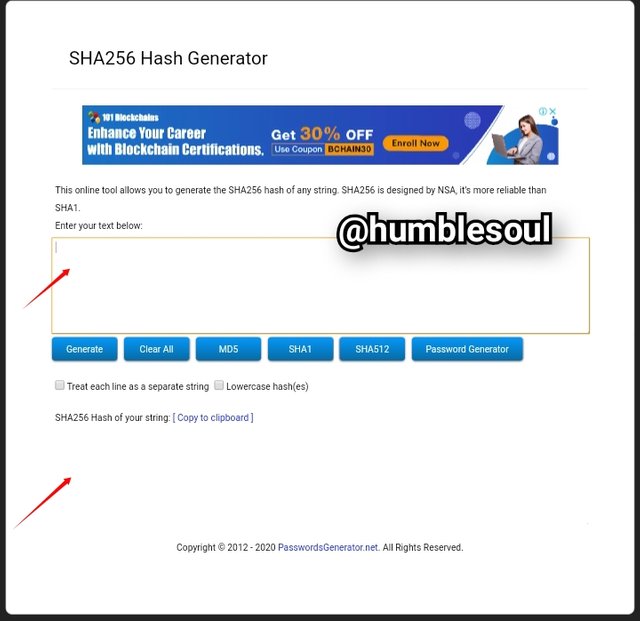
- From the image above, the first space is where a text can be pasted on and then be generated.
2: The word to be generated is filled in the text space (CryptoAcademy)
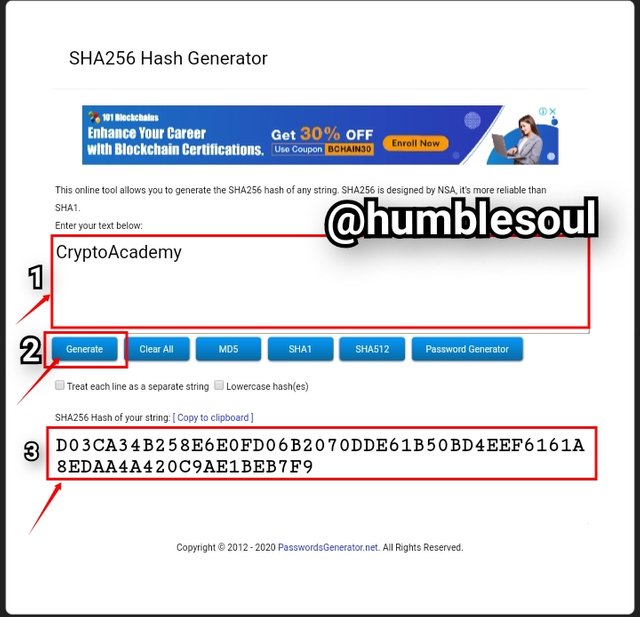
- After generated the following hash was formed:D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
3: The next word to be generated is (cryptoacademy) is filled in the text space as you can see from the image below
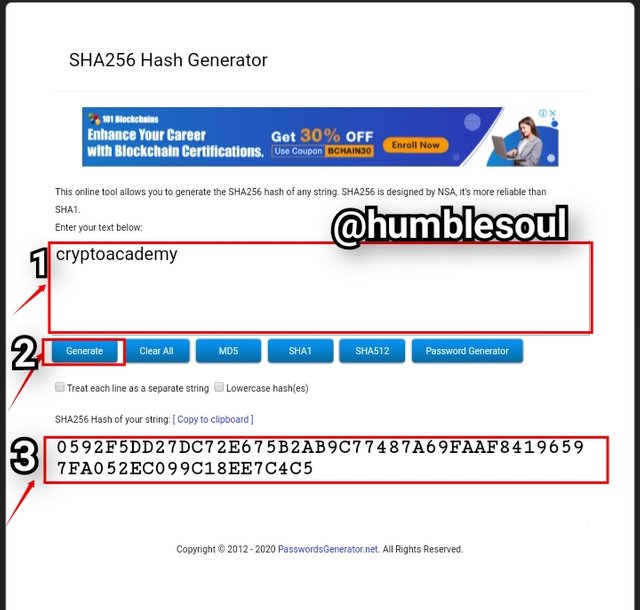
- From the word above, the following hash was formed:0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
THE DIFFERENCE IS CLEAR
Based on the text input CryptoAcademy, The first word of the words above started with an uppercase while the rest alphabet are in lowercases.
Based on the text input cryptoacademy, the words or alphabet are all in lowercases.
N/B: This is peculiar that is why different inputs were generated which prompted the generation of a different hash function despite the similarity in words structure.

IN YOUR OWN WORDS EXPLAIN THE DIFFERENCE BETWEEN HASH AND CRYPTOGRAPHY

Cryptography and hashing has their similarities but desipte that, differences must reflect, which are:
| CRYPTOGRAPHY | HASH |
|---|---|
| Data can be restore with the use of it appropriate keys and algorithm. | Data or information can't be recouped even with the use of any related appropriate keys or means. |
| Data increases in length without the use any fixed duration. | Data has a fixed length of information. |
| Produces same keys for any new information. | Generating of keys (new) in any data creation. |
| Data are encrypted and kept far-off from third-parties. | It's based on indexing of items or informations in tbe database. |
| Security fence is tight and high. | The security is low and easily traspassed by perpetrators. |
CONCLUSIVELY
The innovation of cryptography and hashing has been useful to the crypto world or system because it structure depatching it similarities has a unique funtions that keeps data or information secured and off any third-parties and making sure that transactions and other related information are secured and can still be recover with the aid of cryptography while hashing has it prime reasons of encrypting into data base.
Thnak You professor @pelon53 for the well-detailed lecture, I hope to learn more from you next time, same platform.

Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
👆 Para generar la misma salida. No la misma entrada.
La seguridad de la función hash es alta.
Recomendaciones:
Responda de una forma clara y sencilla, que sea entendible.
Cuando investigue esté atento a los detalles.
Calificación: 7.7
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit